Be a part of prime executives in San Francisco on July 11-12, to listen to how leaders are integrating and optimizing AI investments for fulfillment. Be taught Extra
Attackers in the present day are weaponizing generative AI to steal identities and extort thousands and thousands of {dollars} from victims through deepfakes and pretext-based cyberattacks. Properly-orchestrated assaults that exploit victims’ belief are rising, with the most recent Verizon 2023 Knowledge Breach Investigations Report (DBIR) discovering that pretexting has doubled in only a 12 months. The dangers of compromised identities have by no means been increased, making identification and entry administration (IAM) a board-level subject throughout many corporations in the present day.
Generative AI is the brand new weapon attackers are utilizing to create and launch identity-based assaults. Michael Sentonas, president of CrowdStrike, informed VentureBeat in a latest interview that attackers are continually fine-tuning their tradecraft, seeking to exploit gaps on the intersection of endpoints and identities:
“It’s one of many greatest challenges that individuals wish to grapple with in the present day. I imply, the hacking [demo] session that [CrowdStrike CEO] George and I did at RSA [2023] was to indicate a number of the challenges with identification and the complexity. The explanation why we linked the endpoint with identification and the info that the person is accessing is as a result of it’s a important drawback. And if you happen to can clear up that, you’ll be able to clear up an enormous a part of the cyber drawback that a corporation has.”
Deepfakes and pretexting in the present day; automated, resilient assaults tomorrow
Some deepfake assaults are concentrating on CEOs and company leaders. Zscaler CEO Jay Chaudhry informed the viewers at Zenith Stay 2023 about one latest incident, by which an attacker used a deepfake of Chaudhry’s voice to extort funds from the corporate’s India-based operations. In a latest interview, he noticed that “this was an instance of the place they [the attackers] truly simulated my voice, my sound … Increasingly more impersonation of sound is going on, however you’ll [also] see an increasing number of impersonation of appears and feels.” Deepfakes have develop into so commonplace that the Division of Homeland Safety has issued a information, Rising Threats of Deepfake Identities.
Occasion
Rework 2023
Be a part of us in San Francisco on July 11-12, the place prime executives will share how they’ve built-in and optimized AI investments for fulfillment and averted frequent pitfalls.
Register Now
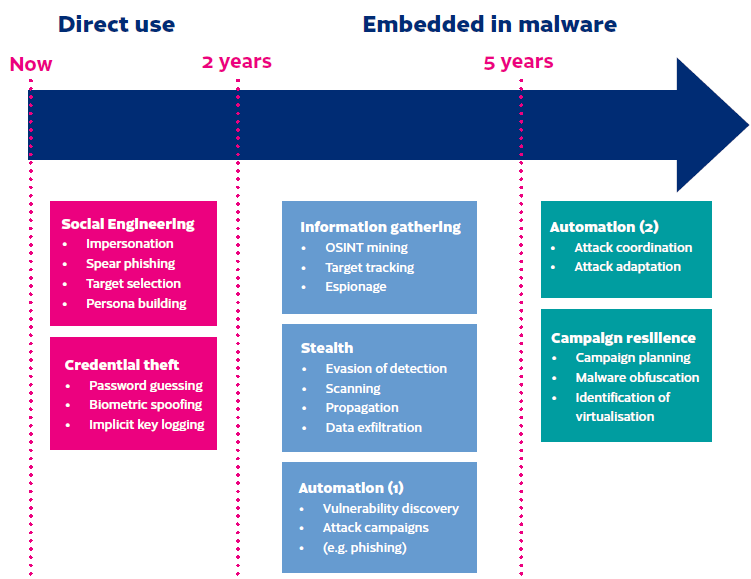
Preying on folks’s belief is how attackers plan on making generative AI pay in the present day. Sentonas, Chaudhry and the CEOs of many different main cybersecurity corporations agree that stolen identities and privileged entry credentials are essentially the most at-risk risk vector that they’re serving to their clients battle. Attackers are betting identification safety stays weak, persevering with to supply an easy-to-defeat entrance door to any enterprise. A examine commissioned by the Finnish Transport and Communications Company, Nationwide Cyber Safety Centre with WithSecure, predicts the way forward for AI-enabled cyberattacks, with a number of the outcomes summarized within the following chart:

Maximize IAM’s effectiveness by constructing on a basis of zero belief
Zero belief is desk stakes for getting IAM proper, and identification is core to zero belief. CISOs should assume a breach has already occurred and go all-in on a zero-trust framework. (Nonetheless, they need to remember that cybersecurity distributors are likely to overstate their zero-trust capabilities.)
“Identification-first safety is important for zero belief as a result of it allows organizations to implement robust and efficient entry controls based mostly on their customers’ wants. By repeatedly verifying the identification of customers and units, organizations can scale back the danger of unauthorized entry and shield in opposition to potential threats,” mentioned CrowdStrike’s George Kurtz. He informed the viewers at his keynote at Fal.Con 2022 that “80% of the assaults, or the compromises that we see, use some type of identification and credential theft.”
Zero belief creator John Kindervag’s recommendation throughout an interview with VentureBeat earlier this 12 months sums up how any enterprise can get began with zero belief. He mentioned, “You don’t begin at a know-how, and that’s the misunderstanding of this. In fact, the distributors wish to promote the know-how, so [they say] it’s good to begin with our know-how. None of that’s true. You begin with a shield floor, after which you determine [the technology].” Kindervag advises that zero belief doesn’t must be costly to be efficient.
What each CISO must learn about IAM in 2023
CISOs inform VentureBeat their most important problem with staying present on IAM applied sciences is the stress to consolidate their cybersecurity tech stacks and get extra finished with much less finances and workers. Ninety-six p.c of CISOs plan to consolidate their safety platforms, with 63% preferring prolonged detection and response (XDR). Cynet’s 2022 CISO survey discovered that just about all have consolidation on their roadmaps, up from 61% in 2021.
CrowdStrike, Palo Alto Networks, Zscaler and different cybersecurity distributors see new gross sales alternatives in serving to clients consolidate their tech stacks. Gartner predicts worldwide spending on IAM will attain $20.7 billion in 2023 and develop to $32.4 billion in 2027, attaining a compound annual progress price of 11.8%. Main IAM suppliers embrace AWS Identification and Entry Administration, CrowdStrike, Delinea, Ericom, ForgeRock, Ivanti, Google Cloud Identification, IBM, Microsoft Azure Energetic Listing, Palo Alto Networks and Zscaler.
VentureBeat has curated 10 features of IAM that CISOs and CIOs have to know in 2023, based mostly on a collection of interviews with their friends over the primary six months of this 12 months:
1. First, audit all entry credentials and rights to close down the rising credential epidemic
Insider assaults are a nightmare for CISOs. It’s one of many worries of their jobs, and one which retains them up at evening. CISOs have confided in VentureBeat {that a} devastating insider assault that isn’t caught may value them and their groups their jobs, particularly in monetary companies. And 92% of safety leaders say inner assaults are as complicated or tougher to establish than exterior assaults.
Importing legacy credentials into a brand new identification administration system is a standard mistake. Spend time reviewing and deleting credentials. Three-quarters (74%) of enterprises say insider assaults have elevated, and over half have skilled an insider risk prior to now 12 months. Eight p.c have had 20 or extra inner assaults.
Ivanti’s lately printed Press Reset: A 2023 Cybersecurity Standing Report discovered that 45% of enterprises suspect that former staff and contractors nonetheless have energetic entry to firm methods and recordsdata. “Massive organizations usually fail to account for the large ecosystem of apps, platforms and third-party companies that grant entry nicely previous an worker’s termination,” mentioned Dr. Srinivas Mukkamala, chief product officer at Ivanti.
“We name these zombie credentials, and an incredibly giant variety of safety professionals — and even leadership-level executives — nonetheless have entry to former employers’ methods and knowledge,” he added.
2. Multifactor authentication (MFA) generally is a fast zero-trust win
CISOs, CIOs and members of SecOps groups interviewed by VentureBeat for this text bolstered how important multifactor authentication (MFA) is as a primary line of zero-trust protection. CISOs have lengthy informed VentureBeat that MFA is a fast win they depend on to indicate constructive outcomes from their zero-trust initiatives.
They advise that MFA have to be launched with minimal disruption to employees’ productiveness. MFA implementations that work greatest mix what-you-know (password or PIN code) authentication with what-you-are (biometric), what-you-do (behavioral biometric) or what-you-have (token) components.
3. Passwordless is the longer term, so begin planning for it now
CISOs should contemplate the best way to transfer away from passwords and undertake a zero-trust method to identification safety. Gartner predicts that by 2025, 50% of the workforce and 20% of buyer authentication transactions will probably be passwordless.
Main passwordless authentication suppliers embrace Microsoft Azure Energetic Listing (Azure AD), OneLogin Workforce Identification, Thales SafeNet Trusted Entry and Home windows Hiya for Enterprise. However CISOs favor Ivanti’s Zero Signal-On (ZSO) answer, as a result of its UEM platform combines passwordless authentication, zero belief and a simplified person expertise.
Ivanti’s use of FIDO2 protocols eliminates passwords and help biometrics together with Apple’s Face ID as secondary authentication components. ZSO will get excessive marks from IT groups as a result of they will configure it on any cell system with out an agent — a large time-saver for ITSM desks and groups.
4. Defend IAM infrastructure with identification risk detection and response (ITDR) instruments
Identification risk detection and response (ITDR) instruments scale back dangers and might enhance and harden safety configurations frequently. They will additionally discover and repair configuration vulnerabilities within the IAM infrastructure; detect assaults; and suggest fixes. By deploying ITDR to guard IAM methods and repositories, together with Energetic Listing (AD), enterprises are enhancing their safety postures and lowering the danger of an IAM infrastructure breach.
Main distributors embrace Authomize, CrowdStrike, Microsoft, Netwrix, Quest, Semperis, SentinelOne (Attivo Networks), Silverfort, SpecterOps and Tenable.
5. Add privileged entry administration (PAM) the the IAM tech stack if it’s not there already
In a latest interview with VentureBeat, Sachin Nayyar, founder, CEO and chairman of the board at Saviynt, commented, “I’ve all the time believed that privileged entry administration belongs within the total identification and entry administration umbrella. It’s a sort of entry that sure customers have a particular want for in any firm. And when it must circulation collectively [with identity access management], there are particular workflows which are particular necessities round session administration, notably compliance necessities, and safety necessities … it’s all a part of the identification administration and governance umbrella in our thoughts [at Saviynt].”
Nayyar additionally famous that he sees robust momentum to the cloud from the corporate’s enterprise clients, with 40% of their workloads operating on Azure because of joint promoting with Microsoft.
6. Confirm each machine and human identification earlier than granting entry to assets
The most recent IAM platforms have agility, adaptability and open API integration. This protects SecOps and IT groups time integrating them into the cybersecurity tech stack. The most recent era of IAM platforms can confirm identification on each useful resource, endpoint and knowledge supply.
Zero-trust safety requires beginning with tight controls, permitting entry solely after verifying identities and monitoring each useful resource transaction. Limiting entry to staff, contractors and different insiders by requiring identification verification will shield from exterior threats.
7. Know that Energetic Listing (AD) is a goal of almost each intrusion
Roughly 95 million Energetic Listing accounts are attacked day by day, as 90% of organizations use the identification platform as their major technique of authentication and person authorization.
John Tolbert, director of cybersecurity analysis and lead analyst at KuppingerCole, writes within the report Identification & Safety: Addressing the Fashionable Menace Panorama: “Energetic Listing parts are high-priority targets in campaigns, and as soon as discovered, attackers can create further Energetic Listing (AD) forests and domains and set up trusts between them to facilitate simpler entry on their half. They will additionally create federation trusts between fully totally different domains.
“Authentication between trusted domains then seems reliable, and subsequent actions by the malefactors will not be simply interpreted as malicious till it’s too late, and knowledge has been exfiltrated and/or sabotage dedicated.”
8. Forestall people from assuming machine roles in AWS by configuring IAM for least privileged entry
Keep away from mixing human and machine roles for DevOps, engineering and manufacturing workers and AWS contractors. If function project is finished incorrectly, a rogue worker or contractor may steal confidential income knowledge from an AWS occasion with out anybody understanding. Audit transactions, and implement least privileged entry to forestall breaches. There are configurable choices in AWS Identification and Entry Administration to make sure this degree of safety.
9. Shut the gaps between identities and endpoints to harden IAM-dependent risk surfaces
Attackers are utilizing generative AI to sharpen their assaults on the gaps between IAM, PAM and endpoints. CrowdStrike’s Sentonas says his firm continues to concentrate on this space, seeing it as central to the way forward for endpoint safety. Ninety-eight p.c of enterprises confirmed that the variety of identities they handle is exponentially rising, and 84% of enterprises have been victims of an identity-related breach.
Endpoint sprawl makes identification breaches more durable to cease. Endpoints are sometimes over-configured and susceptible. Six in 10 (59%) endpoints have a minimum of one identification and entry administration (IAM) agent, and 11% have two or extra. These and different findings from Absolute Software program’s 2023 Resilience Index illustrate how efficient zero-trust methods are. The Absolute report finds that ” zero-trust community entry (ZTNA) helps you [enterprises] transfer away from the dependency on username/password and as a substitute depend on contextual components, like time of day, geolocation, and system safety posture, earlier than granting entry to enterprise assets.”
The report explains, “What differentiates self-healing cybersecurity methods is their relative skill to forestall the … components that they’re constructed to guard in opposition to: human error, decay, software program collision, and malicious actions.”
10. Resolve to excel at just-in-time (JIT) provisioning
JIT provisioning, one other foundational factor of zero belief, reduces dangers and is constructed into many IAM platforms. Use JIT to restrict person entry to tasks and functions, and shield delicate assets with insurance policies. Limiting entry improves safety and protects delicate knowledge. JIT enhances zero belief by configuring least privileged entry and limiting person entry by function, workload and knowledge classification.
Your first precedence: Begin by assuming identities are going to be breached
Zero belief represents a elementary shift away from the legacy perimeter-based approaches organizations have relied on. That’s as a result of working methods and the cybersecurity purposes supporting them assumed that if the perimeter was safe, all was nicely. The other turned out to be true. Attackers rapidly discovered the best way to fine-tune their tradecraft to penetrate perimeter-based methods, inflicting a digital pandemic of cyberattacks and breaches.
Generative AI takes the problem to a brand new degree. Attackers use the most recent applied sciences to fine-tune social engineering, enterprise e-mail compromise (BEC), pretexting, and deepfakes that impersonate CEOs, all geared toward buying and selling on victims’ belief. “AI is already being utilized by criminals to beat a number of the world’s cybersecurity measures,” warns Johan Gerber, govt vice chairman of safety and cyber innovation at MasterCard. “However AI must be a part of our future, of how we assault and deal with cybersecurity.”
The underside line: Zero belief stops breaches day by day by imposing least privileged entry, validating identities, and denying entry when identities can’t be verified.
>>Observe VentureBeat’s ongoing generative AI protection<<