Try all of the on-demand classes from the Clever Safety Summit right here.
CISOs inform VentureBeat they’re seeking to get extra worth from safety operations (SecOps) by figuring out threats somewhat than analyzing them after an occasion. Gartner’s course is that “SecOps’ aim is to create proactive danger understanding and allow menace publicity discount in addition to detection of, and response to, cyber occasions that negatively have an effect on the group.”
SecOps groups need assistance to get out of a reactive strategy of analyzing alerts and intrusion, breach and botnet occasions after they’ve occurred. As a primary step to fixing this problem, enterprise safety groups and the CISOs that lead them are pushing for larger real-time visibility. As well as, tech-stack consolidation, a powerful deal with minimizing prices, and the necessity to rise up distant SecOps places sooner than on-premises techniques and their infrastructure permit are driving SecOps groups’ want for menace intelligence and extra real-time information.
Enhancing SecOps with real-time menace intelligence
For SecOps to ship on its potential, it should begin by lowering false positives, filtering out inbound noise, and offering menace intelligence that triggers automated detection and remediation actions. Briefly, SecOps groups want menace intelligence suppliers to interpret and act on inbound packets instantly, discovering new methods to capitalize on real-time information. Happily, the subsequent era of menace intelligence options is purpose-built to offer post-attack analytics, together with forensic visibility throughout all occasions.
The Nationwide Institute of Requirements and Know-how (NIST) defines menace intelligence as “menace data that has been aggregated, reworked, analyzed, interpreted, or enriched to offer the mandatory context for decision-making processes.” NIST mentions menace intelligence of their NIST SP 1800-21, NIST SP 800-150, and NIST SP 800-172A requirements.
Occasion
Clever Safety Summit On-Demand
Study the essential position of AI & ML in cybersecurity and business particular case research. Watch on-demand classes at this time.
Watch Right here
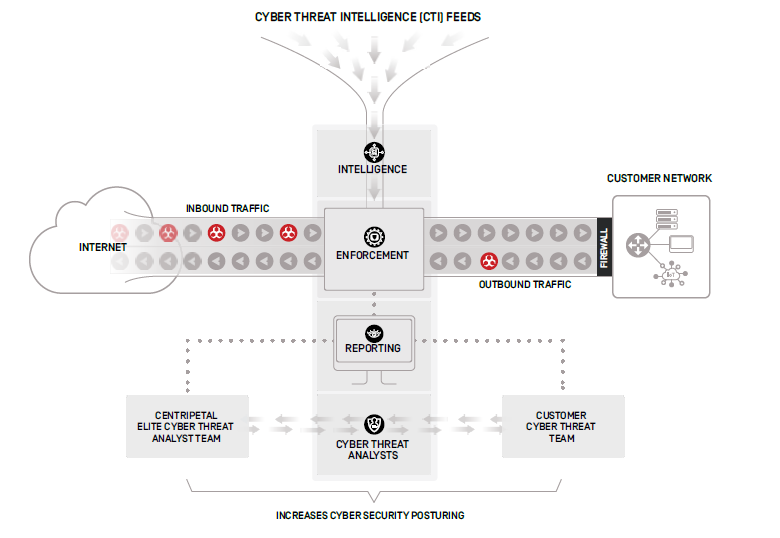
Main distributors embody Centripetal, whose CleanINTERNET answer operationalizes cyberthreat intelligence at scale by combining automated shielding, superior menace detection (ATD) and devoted groups of human menace analysts. Centripetal’s buyer base contains authorities businesses, monetary establishments, healthcare suppliers and demanding infrastructure suppliers.
“Menace intelligence, in the event you apply it correctly, can turn into a extremely efficient instrument to find out mechanically who ought to come into your community and who shouldn’t, and thus provides a corporation risk-based management,” mentioned Centripetal’s CEO, Steven Rogers.
There are greater than 75 distributors within the menace intelligence market at this time, together with CrowdStrike, Egnyte, Ivanti, Mandiant, Palo Alto Networks, and Splunk. All try to strengthen their menace intelligence as core to their capability to contribute to their prospects’ SecOps wants.
Centripetal’s structure is noteworthy in its use of synthetic intelligence (AI) and proprietary algorithms to combination, filter, correlate, detect, triage and analyze 1000’s of worldwide feeds at huge scale and machine pace. AI acts as an orchestration expertise of their platform, coordinating menace intelligence feeds and enforcement algorithms and concurrently reporting to each Centripetal’s inner cyberthreat analyst staff and that of the client.

Scaling menace intelligence within the enterprise
VentureBeat lately sat down just about with Chuck Veth, president of CVM, Inc., to learn the way enterprises are placing menace intelligence to work and the way his agency helps their implementations scale. CVM, an IT companies agency with greater than 30 years of expertise, is a two-time winner of Deloitte’s CT Quick 50. Chuck’s agency implements and helps Centripetal and is a number one reseller to enterprise and authorities accounts. Offered listed below are chosen segments of VentureBeat’s interview with Chuck:
VentureBeat: What challenges do your prospects face that led you to contact Centripetal to be a reseller for them?
Chuck Veth: “The problem to boost cybersecurity is fixed. We first realized about Centripetal from one among our accounts. After evaluating it and presenting it to our prospects, we realized that the CleanINTERNET service is a wonderful ultimate layer of safety for public-facing networks. We have a look at it as a crucial insurance coverage coverage. While you activate CleanINTERNET, it will get used 1000’s of instances a minute.”
VB: Conserving with the insurance coverage analogy, are you able to broaden on the way you see the worth Centripetal gives?
Veth: “It’s not like automobile insurance coverage; you are able to do the mathematics simply on asset safety insurance coverage. It’s extra just like the automobile insurance coverage part that covers harm to the occupants, which you usually don’t take into consideration if you’re evaluating automobile insurance coverage. You’re fascinated about your automobile. However the reality is, automobile insurance coverage is absolutely there for the individuals as a result of they’re irreplaceable. When fascinated about community safety, you primarily strategy it from the packet inspection perspective. Centripetal’s CleanINTERNET service works from a very totally different perspective. It’s figuring out if the distant IP deal with is a menace actor; whether it is, it blocks it. It is advisable use this attitude as properly; the price of lacking a menace actor can shut your corporation.”
VB: What are a few of the most dear classes realized concerning how Centripetal gives larger menace intelligence of your shared prospects with them?
Veth: “Some of the thrilling outcomes of getting the Centripetal CleanINTERNET service is its capability to separate a menace actor from a non-threat actor on some quite common pathways of the web. HTTPS visitors travels on port 443, HTTP on port 80, and e mail travels on port 25, et cetera. Years in the past, when some companies lived on comparatively distinctive ports, they have been straightforward to watch for an assault. In the present day it’s more durable because the business has moved to a world that lives on a handful of ports, like 443, utilizing SSL certificates.
“For instance, people on non-public networks usually flip to public proxy server web sites to keep away from company filtering, akin to blocking day buying and selling. The person connects to the proxy service, and it connects their browser to the day buying and selling website. All of the person must do is discover a proxy service that’s not blocked by their firm firewall. Dangerous actors usually function these proxy companies as they’ll observe each element of the net exercise.”
VB: That’s the hazard of utilizing a proxy service that isn’t verified to go to a website your organization has blocked. How does menace intelligence assist determine the menace and shield infrastructure?
Veth: “Centripetal is trying on the IP deal with and saying, ‘I’ve an inventory of billions of IP addresses which can be recognized to be operated by menace actors.’ It’s a special means of issues. And, to do it appropriately, Centripetal compiles real-time data from lots of upon lots of, even 1000’s, of menace intelligence feeds. And that’s the key sauce of the Centripetal CleanINTERNET service. They’re normalizing the information from 1000’s of real-time menace intelligence feeds to say, ‘Hey, this explicit website popped up in three or 4 totally different menace intelligence databases. And for us, that could be a signal that it’s a menace actor. And so, we’re going to dam it.’”
VB: What’s your favourite instance of how efficient Centripetal is at uncovering dangerous actors’ assault methods which can be cloaked to keep away from detection?
Veth: “In the future, we obtained a word from our Centripetal safety analyst, ‘…this menace actor’s attempting to speak with this buyer – it’s a recognized menace actor working out of Europe – it’s this IP deal with….’ We’re an IT agency, so we regarded up the IP deal with, and the IP deal with was at a internet hosting facility in New York.
“And we’re like, ‘What? Why did our safety analyst inform us that this IP deal with was on this overseas nation when one among our employees discovered that it’s in New York?’ We browsed to the IP deal with. It was a internet hosting firm in New York that solely takes cost through cryptocurrency and requires no audit to host on its service. So any host can join this service with no authentication. However the Centripetal system knew that this website, though hosted in New York, was a menace actor from a overseas nation. This might have by no means been blocked by geofiltering, however the Centripetal service was in a position to determine it and block it.”
How menace intelligence permits zero belief
Having menace intelligence add worth in a zero-trust framework requires figuring out and classifying threats earlier than they acquire entry to a company community. Deciphering each information packet after which evaluating its degree of danger or belief is crucial — whereas factoring in and correlating to all recognized world menace feeds in an adaptive, customizable service. Figuring out and classifying threats earlier than they attain the community is core to the way forward for menace intelligence and the power for SecOps emigrate to a zero-trust framework.
Menace intelligence must do the next to extend its worth to zero-trust initiatives:
Implement zero belief by inspecting each packet of bidirectional visitors
Distributors are setting service objectives that middle on their capability to defend their prospects’ organizations from all recognized assaults. Every of the competing distributors in menace intelligence is taking a special strategy.
Frequently enhance the real-time visibility throughout the recognized threatscape
Most menace intelligence distributors are extra targeted on analyzing the information from earlier occasions. A number of have confirmed distinctive in utilizing machine studying algorithms to take a look at predictive patterns in visitors and assault information. What’s wanted is a menace intelligence system that may combination the information of each inbound packet, then correlate the evaluation outcomes with recognized threats. Centripetal compares every packet’s contents to all accessible cyberthreat indicators in actual time, utilizing 1000’s of worldwide menace feeds to assist their single, totally managed service.
Scale back false positives, inaccurate alerts and occasions by verifying each entry try earlier than it will get inside the company community
A core tenant of zero belief is to imagine the community has already been breached and the attacker must be contained to allow them to’t laterally transfer into core techniques and do harm. Main menace intelligence system suppliers are making use of machine studying algorithms to scale back the noise from exterior networks, filtering out extraneous information to search out the precise threats. Moreover contributing to the zero-trust initiatives of a corporation, it helps cut back the burden on the safety operations middle (SOC) in having to clear false positives and alerts.
SecOps should enhance at delivering business-driven outcomes based mostly on real-time information insights, studying to be extra adaptive and faster to reply at scale. As a part of the subsequent era of menace intelligence options, firms like Centripetal assist SecOps groups by specializing in offering menace intelligence to scale back false positives, filter out inbound noise and set off automated detection and remediation actions.