Be a part of high executives in San Francisco on July 11-12, to listen to how leaders are integrating and optimizing AI investments for fulfillment. Be taught Extra
One compromised browser session on a distant machine related to a corporation’s community can shut a whole enterprise down. As one CISO confided to VentureBeat in a current interview, “Recessions make the income danger features of a zero-trust enterprise case actual, exhibiting why securing browsers deserves urgency.” Greater than anything, CISOs from the banking, monetary companies and insurance coverage industries worry inbound assaults aimed toward exploiting browsers’ weaknesses to launch subtle phishing and social engineering assaults.
Attackers can shortly establish and hack even safety directors’ browsers — any CISOs’ worst nightmare. Many CISOs recall the CNA Monetary Company breach that began with a phishing e-mail browser replace. As soon as an attacker beneficial properties admin rights, they will shortly take management of the id entry administration (IAM) programs and create new admin credentials to lock out anybody attempting to cease them.
CISOs’ highest precedence: Securing how work will get finished
Defending bring-your-own-device (BYOD) environments and unmanaged gadgets is one among CISOs’ and CIOs’ greatest challenges in 2023. Digital staff and third-party contractors are utilizing private gadgets for work at file charges. Gartner forecasts that as much as 70% of enterprise software program interactions will happen on cellular gadgets this 12 months.
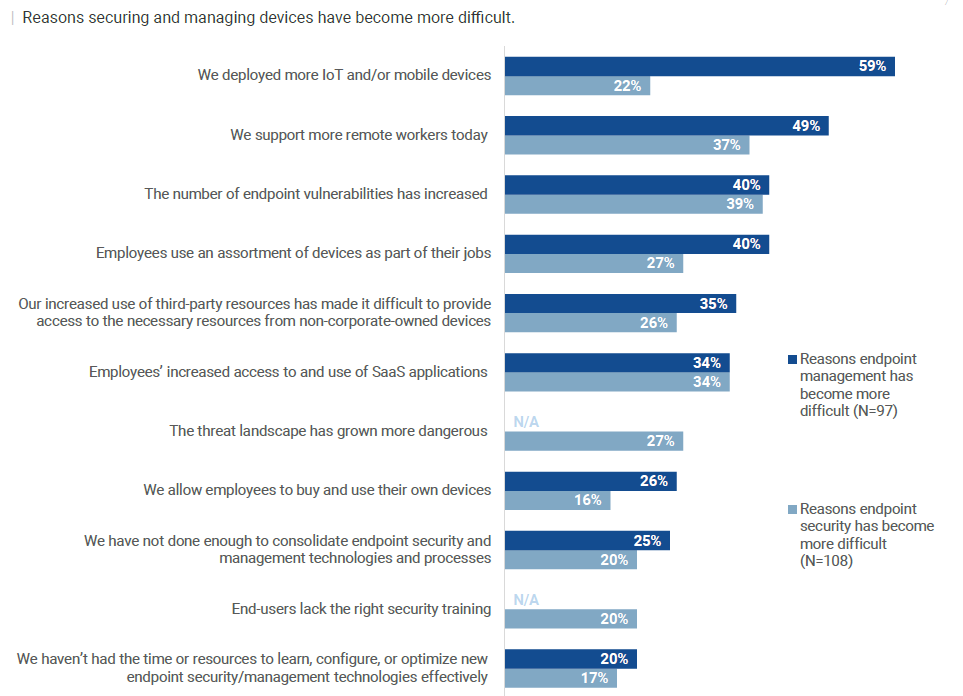
Ponemon Institute and Mastercard’s RiskRecon discovered that solely 34% of organizations are assured their distributors would notify them of an information breach. Their examine additionally discovered that 54% of organizations have been breached via third events within the final 12 months. A current analysis examine by Enterprise Technique Group (ESG) discovered that greater than three-quarters of organizations reported having skilled at the least one (43%) or a number of (34%) cyberattacks allowed by unknown, unmanaged or poorly managed endpoint gadgets. As they use extra third-party assets, 35% of corporations say they battle to safe non-corporate-owned gadgets.
Occasion
Rework 2023
Be a part of us in San Francisco on July 11-12, the place high executives will share how they’ve built-in and optimized AI investments for fulfillment and averted frequent pitfalls.
Register Now

A playbook to take care of browser assaults
CISOs urgently want a playbook that addresses the chance of compromised browser periods on distant gadgets related to their group’s community. Not having a plan prepared might disrupt operations and price tens of millions of {dollars} in working prices and income.
A playbook describes the corporate’s workflows, insurance policies and roles. It’s a complete information that ensures clean operation and coordinated response to threats. Microsoft offers examples of incident response playbooks that may be tailor-made to a corporation’s particular wants.
A well-crafted playbook outlines the IT workforce’s roles and tasks; implements strict entry controls; and educates staff on phishing and social engineering greatest practices to handle these dangers.
The playbook must also emphasize a zero-trust cybersecurity method, the place no person or machine is trusted by default, no matter location or standing within the group.
CISA offers a useful information to creating playbooks in its Cybersecurity Incident & Vulnerability Response Playbooks doc. The doc describes a standardized cybersecurity incident response course of based mostly on NIST Particular Publication (SP) 800-61 Rev. 2. The method contains preparation, detection and evaluation, containment, eradication, restoration and post-incident actions.

Securing the place work will get finished with zero belief
Zero belief seeks to get rid of trusted relationships throughout an enterprise’s expertise stack — as a result of any belief hole is a big legal responsibility. Clientless zero-trust community entry (ZTNA) takes a zero-trust method to connecting gadgets, whether or not managed or unmanaged, to enterprise purposes and company knowledge. And when it makes use of isolation-based applied sciences to allow these connections, it brings the extra advantage of defending key purposes from something that is perhaps malicious on unmanaged endpoints of third-party contractors or staff’ BYOD gadgets.
For instance, clientless ZTNA based mostly on browser isolation is a core part of Ericom’s ZTEdge safe companies edge (SSE) platform. The platform combines community, cloud and safe utility entry safety controls in a single cloud-based system.
The sort of ZTNA makes use of a network-level isolation method that doesn’t require any agent to be deployed and managed on a person’s machine. That significantly simplifies the difficult job of offering safe entry to distributed groups.
Ericom’s platform additionally features a safe net gateway (SWG) with built-in distant browser isolation (RBI) to offer zero-trust safety for net shopping. RBI assumes that each one web sites might include malicious code and isolates all content material from endpoints to stop malware, ransomware and malicious scripts or code from impacting a corporation’s programs. All periods are run in a safe, remoted cloud atmosphere, implementing least-privilege utility entry on the browser session degree.
A reseller’s perspective on clientless ZTNA and isolation-powered net safety
Rob Chapman, managed companies gross sales director at Flywheel IT Companies Restricted, a cybersecurity companies reseller based mostly within the U.Okay., informed VentureBeat of 1 CISO who “is even saying that he wants to make use of distant browser isolation as a result of the one secure different could be to cut each person’s fingers off!”
Chapman sees RBI as the place the market goes in terms of defending finish customers. He mentioned that Ericom’s method to securing browsers is useful for the consultancy’s shoppers from the banking, monetary companies and training industries, amongst others.
When requested what differentiates Ericom from different distributors offering zero trust-based options, he mentioned Ericom’s method “successfully removes danger since you are containerizing the person.”
Getting scalability proper is important for an SSE supplier that wishes to remain aggressive in a fast-moving cybersecurity market. Constructing an underlying structure that helps the quick entry that enterprise customers require could make or break an implementation alternative, particularly for resellers.
On this subject, Chapman informed VentureBeat that one world buyer “determined to go along with [browser isolation] as a result of they’ve received a set of 600 customers and 20 totally different websites world wide, and it’s simply very, very troublesome to know that you just’re securing them in addition to potential with historic … or legacy options. Going to superior net safety that features browser isolation offers folks the arrogance that their customers will not be going out and being uncovered to malicious code assaults on the web.”
Configuring zero belief safety within the browser — with out agent sprawl
When utilizing browser isolation to ship clientless ZTNA, IT groups can set coverage throughout a lot of configurable safety controls.
Along with allowing or denying application-level entry based mostly on id, a workforce can management a person’s skill to add or obtain content material, copy knowledge, enter knowledge and even print info.
Knowledge loss prevention (DLP) can scan recordsdata to make sure compliance with info safety insurance policies. They can be analyzed by content material disarm and reconstruction (CDR) — a kind of next-generation sandboxing — to verify malware is just not introduced onto endpoints or uploaded into purposes.
CISOs inform VentureBeat of the fee, pace and zero-trust safety benefits of deploying some of these options throughout distributed, digital workforces.
Cybersecurity distributors supply options that fluctuate by underlying applied sciences, person expertise and different components. Broadcom/Symantec, Cloudflare, Ericom, Forcepoint, Iboss, Menlo Safety, McAfee, NetSkope and Zscaler are the main suppliers.

The underside line: Instituting zero belief to safe how and the place work will get finished
The proliferation of distant gadgets utilized by digital workforces and heavy reliance on third-party contractors intensify the necessity for extra environment friendly, agentless approaches to reaching zero belief on the browser degree.
CISOs want to contemplate how their groups can reply to a browser-based breach, and a good way to start out is by making a playbook particularly centered on compromised browser periods.
Clientless ZTNA methods like these utilized in Ericom’s ZTEdge SSE platform isolate purposes and company knowledge from the dangers related to unmanaged gadgets.
Safety groups which might be already stretched skinny and dealing with power time shortages want a extra environment friendly technique to safe each machine and browser. Clientless ZTNA secures net apps on the browser and session ranges and eliminates the necessity for brokers on each machine, whereas SWGs with isolation in-built assist defend organizations from superior net threats, even zero-days.
These approaches will help IT groups carry zero-trust safety to a number of the greatest danger areas they face — normal net/web entry, and connecting customers to company apps and knowledge.