Be a part of prime executives in San Francisco on July 11-12, to listen to how leaders are integrating and optimizing AI investments for achievement. Be taught Extra
Statistics from 2022 and into 2023 present the cybersecurity trade has extra work to do to people-proof assault vectors. Attackers are capitalizing on stolen credentials, privilege misuse, human error, well-orchestrated social engineering, enterprise e mail compromise (BEC) and, doubling in only a yr, pretexting. Each cybersecurity supplier must step up efforts to enhance id, privileged entry, and endpoint safety to ship the worth their prospects want. Organizations should transfer past coaching and act to supply a powerful protection baseline.
Attackers are discovering new methods to dupe victims for {dollars}
Verizon’s 2023 Knowledge Breach Investigations Report (DBIR) displays how briskly the threatscape is evolving to prey on individuals’s good nature. We frequently need to assist colleagues, family and friends once they request money or different types of monetary assist. VentureBeat has discovered of dozens of tech corporations routinely attacked with pretexting as a part of orchestrated social engineering assaults. The well-known reward card rip-off has turn out to be so commonplace that the Federal Commerce Fee revealed steerage on keep away from it. In line with Web Crime Criticism Heart (IC3) information, the median theft quantity for BEC has elevated to $50,000.
Extra funds, extra breaches
One of the crucial highly effective takeaways from the report is that regardless of elevated spending, cybersecurity shouldn’t be pivoting quick sufficient to guard individuals from superior pretexting assaults. The reply to this problem isn’t to double spending on coaching or, worse, proceed the ineffective follow of making an attempt to trick staff with faux phishing emails.
As an alternative, corporations can be safer in the event that they first assumed a breach would occur, then took preventative measures earlier than one did. Getting fundamental cybersecurity hygiene proper at scale and implementing zero belief incrementally, defending one floor at a time, is what cybersecurity skilled John Kindervag suggested organizations to start out with throughout a latest interview with VentureBeat. Kindervag suggested enterprises to not shield all surfaces concurrently, however to choose as a substitute for an iterative method, telling VentureBeat that it is a confirmed solution to scale zero belief with out asking the board to fund a capital equipment-level funding.
Occasion
Rework 2023
Be a part of us in San Francisco on July 11-12, the place prime executives will share how they’ve built-in and optimized AI investments for achievement and averted widespread pitfalls.
Register Now
10 key takeaways
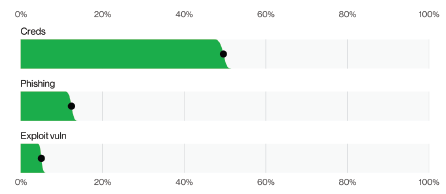
Attackers’ fine-tuned methods are moving into victims’ heads and shortening the time from preliminary contact to when a goal truly falls sufferer. Stolen privileged entry credentials proceed to be a favourite approach for attackers to realize entry to techniques and mix into common system visitors undetected. Verizon discovered stolen credential use elevated from 41.6% to 44.7% of all breaches in only a yr.
Listed here are the highest 10 key takeaways of the Verizon 2023 DBIR:
Eighty-three % of breaches are initiated by exterior attackers searching for fast monetary achieve. Organized crime gangs and networks provoke eight out of each 10 breaches, 95% of the time for monetary achieve. Smash-and-grab assaults on buyer and monetary information are commonplace, with ransomware the weapon of alternative.
The monetary providers and manufacturing sectors prime attackers’ hit lists, as these companies should ship services on time to maintain prospects and survive. And other people have turn out to be the preliminary risk floor of alternative, with pretexting, coordinated with social engineering, the preliminary assault technique.
Eighty-four % of breaches goal people because the assault vector, utilizing social engineering and BEC methods. In line with the final two Verizon DBIR studies, many breaches contain human error. In line with this yr’s report, 74% of breaches started by human error, social engineering or misuse. In final yr’s report the determine was an excellent greater 82%. However the yr earlier than that, the 2021 DBIR discovered that simply 35% of profitable breaches began that approach.
One out of each 5 breaches, 19%, originate from the within. CISOs inform VentureBeat that insider assaults are their worst nightmare as a result of figuring out and stopping these sorts of breaches is so difficult. That’s why main distributors with AI and machine studying experience have insider risk mitigation on their roadmaps. Booz Allen Hamilton makes use of information mesh structure and machine studying algorithms to detect, monitor and reply to suspicious community exercise. Proofpoint is one other insider risk detection vendor that makes use of AI and machine studying. Proofpoint’s ObserveIT offers real-time alerts and actionable insights into person exercise.
A number of distributors are both exploring or have acquired corporations for strengthening their platforms in opposition to insider threats. An instance is CrowdStrike’s acquisition of Reposify final yr, introduced at CrowdStrike’s annual Fal.Con occasion. Reposify scans the net each day, looking for uncovered property to present organizations visibility over them, and defining the actions they should take to remediate them. CrowdStrike plans to combine Reposify’s know-how into the CrowdStrike platform to assist prospects cease inside assaults.
System intrusion, fundamental net software assaults and social engineering are among the many main assault methods. Two years in the past, within the 2021 DBIR Report, fundamental net software assaults accounted for 39% of breaches and have been 89% financially motivated. Phishing and BECs have been additionally prevalent and financially motivated (95%) that yr. In distinction, this yr’s 2023 Verizon DBIR discovered that system intrusion, fundamental net software assaults and social engineering accounted for 77% of data trade breaches, most of which have been financially motivated.
The development of elevated net software assaults is rising, as evidenced by the expansion seen in simply two years of knowledge from Verizon. This underscores the necessity for more practical adoption of zero-trust-based distant browser isolation (RBI) throughout enterprises. Main distributors on this space embrace Broadcom/Symantec, Cloudflare, Ericom, Forcepoint, iboss, Menlo Safety, MacAfee, NetSkope and Zscaler. Ericom’s ZTEdge, for instance, makes use of net software isolation as a clientless zero belief community entry (ZTNA) method that secures BYOD and unmanaged machine entry to company net and SaaS apps.

System intrusion is an assault technique utilized by extra skilled attackers with entry to malware to breach enterprises and ship ransomware. Final yr’s Verizon DBIR confirmed system intrusion to be the highest incident class, changing fundamental net software assaults, which was the highest incident class in 2021.

Social engineering assaults’ sophistication is rising quick, as evidenced by pretexting’s fast progress. This yr’s DBIR highlights how worthwhile social engineering assaults have turn out to be and the way refined pretexting is right this moment. BEC and pretexting assaults have practically doubled throughout all the incident dataset and now account for greater than 50% of social engineering incidents. Compared, the 2022 Verizon DBIR discovered that social engineering assaults have been accountable for 25% of breaches. In 2021, Verizon discovered that BECs have been the second commonest sort of social engineering, and misrepresentation has grown 15 occasions greater over the previous three years.
Ninety-five % of breaches in 2023 are financially pushed, countering the hype about nation-state espionage. As attackers hone their social engineering tradecraft, the share of financially motivated breaches will increase. Trending information from earlier studies present how monetary achieve is rising as a major motivation over company espionage or revenge assaults by former staff. The 2022 Verizon DBIR had discovered that 90% of all attackers initiated a breach for monetary achieve, up from 85% in 2021.
The bounce might be attributed to greater potential ransomware payouts, mixed with multi-attack methods with the next chance of success. There’s additionally the likelihood that espionage assaults aren’t being detected as a lot as a consequence of attackers realizing steal privileged entry credentials and breach networks undetected for months.
The median value to victims per ransomware incident greater than doubled over the previous two years to $26,000, with 95% of incidents leading to a lack of between $1 and $2.25 million. Ransomware payouts proceed to set information as attackers go after the industries with essentially the most to lose from shutdowns. It’s not stunning to see monetary providers and manufacturing among the many hardest-hit industries, as this yr’s DBIR studies.
For the 2021 DBIR, Verizon used FBI information and located that the median ransomware payout was $11,150. In 2020, ransomware payouts had averaged $8,100, and that was up from simply $4,300 in 2018. So in 5 years, common ransomware payouts have tripled.

Twenty-four % of breaches concerned ransomware this yr, persevering with its long-term upward development as a major assault technique. Ransomware was found in 62% of all incidents dedicated by organized-crime attackers and 59% of all incidents with a monetary aim within the 2023 DBIR. Verizon’s 2022 evaluation had discovered ransomware breaches leaping 13% from the earlier yr. Persevering with the development and gaining momentum, ransomware assaults greater than doubled between 2022 and 2023, rising from 25% of all information breaches to 62% this yr.
Over 32% of all Log4j vulnerability scanning occurred within the first 30 days after launch. Verizon’s newest DBIR discovered that exploits peaked 17 days after attackers found a flaw. The short exploitation of Log4j vulnerabilities exhibits why organizations should reply sooner to new threats. They need to prioritize patching and updating techniques as vulnerabilities are found. This consists of making use of all software program and system safety patches. A strong vulnerability administration program may also help organizations determine and repair vulnerabilities earlier than attackers can exploit them.

Seventy-four % of monetary and insurance coverage trade breaches concerned compromised private information — main all industries by a large margin. Compared, different industries skilled considerably much less private information being compromised: 34% of lodging and meals providers trade breaches have been the results of compromised private information, and for the academic providers trade, the determine was 56%.
Attackers continuously goal monetary establishments with credential and ransomware assaults, which explains why the trade leads all others in compromised private information assaults.
Wanting again, in combination throughout all industries, 83% of 2021 breaches have been the results of compromised private information. And within the 2022 Verizon DBIR, net software assaults, system intrusion and miscellaneous errors precipitated 79% of monetary and insurance coverage breaches.
Cybersecurity spending is a enterprise funding in belief
This yr’s DBIR gives a stark reminder of how attackers are altering the threatscape with pretexing and superior types of digital fraud. The report’s most important discovering is that, regardless of elevated cybersecurity spending, breaches have gotten extra frequent and complex, highlighting the necessity for a extra built-in, unified method to cybersecurity that doesn’t go away id safety to probability.
Unsurprisingly, 24% of breaches contain ransomware, displaying that attackers are more and more concentrating on industries with essentially the most to lose from enterprise interruptions. Ransomware incidents have elevated in value, making backup and incident response methods extra obligatory to reduce harm. The DBIR’s report on the Log4j vulnerability’s fast exploitation highlights the necessity to act rapidly to handle new threats, partially by rushing up patching and system updates.
In conclusion, the Verizon 2023 DBIR report emphasizes the necessity for organizations to rethink their cybersecurity methods. They need to think about human components, together with insider threats, and how briskly assault methods evolve. Enterprises should create a cybersecurity tradition that goes past IT departments, one which promotes vigilance, resilience and fixed adaptation to evolving threats.