Head over to our on-demand library to view classes from VB Remodel 2023. Register Right here
The fast rise in cyberattacks delivering malicious payloads, together with ransomware, occurs as a result of organizations have change into too complacent with legacy IAM, VPN, and perimeter-based community safety methods. CISOs inform VentureBeat that hardware-based methods, by no means designed to guard past perimeters, can’t establish the newest ransomware and malware-free assaults and have now change into a legal responsibility.
Proving how deadly it’s to depend on legacy know-how that may’t establish the newest threats, CrowdStrike’s newest analysis discovered that 71% of all detections listed by CrowdStrike Risk Graph are malware-free.
From attackers performing alone to large-scale operations financed via organized crime and nation-states, each attacker is aware of that legacy VPN, endpoint, and perimeter methods can’t see a malware-free assault, their assault methods or their payloads.
The extra siloed safety methods are, the higher the chance that an attacker will get in and stays undetected, in some circumstances for years, as a result of a company trusted in perimeter safety for too lengthy and received compromised. Major targets that attackers go after immediately embrace healthcare and manufacturing as a result of even the slightest slowdown might value lives and probably destroy the enterprise.
Occasion
VB Remodel 2023 On-Demand
Did you miss a session from VB Remodel 2023? Register to entry the on-demand library for all of our featured classes.
Register Now
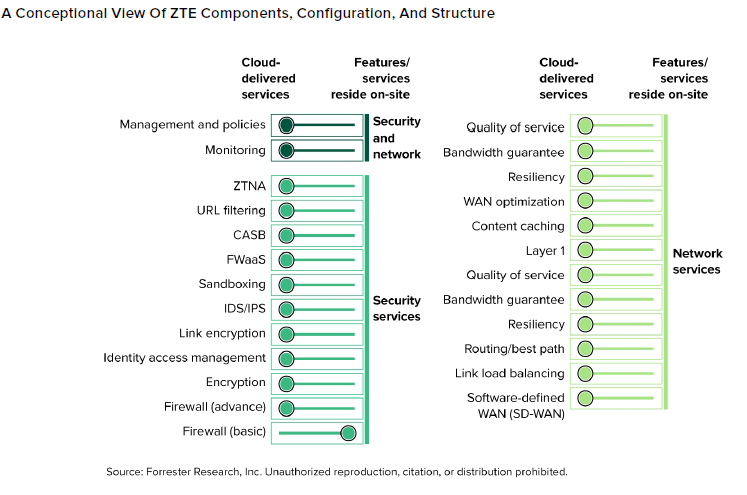
Forrester’s current report, The Zero Belief Edge Options Panorama, Q2 2023, offers insights and helpful evaluation of how CISOs can migrate away from dangerous legacy tech stacks that depend on outdated perimeter safety approaches and higher safe their IT infrastructure with Zero Belief Edge (ZTE). Forrester’s research reveals that the important thing drivers behind ZTE adoption embrace the shift to distant work and distributed property, elevated enterprise velocity and disruptive distributors providing built-in community/safety, together with profiles of twenty-two of the main distributors available in the market.
Barracuda Networks, Cato Networks, Cisco Methods, Cloudflare, Cradlepoint, Forcepoint, Fortinet, Google, HPE Aruba Networking, Huawei, iBoss, Juniper Networks, Lookout, Menlo Safety, Netskope, Nokia, Open Methods, Palo Alto Networks, Sophos, Versa Networks and VMware Zscaler are included within the report.
Closing Cloud, IoT, and remote-work gaps must occur now
Attackers are out-innovating enterprises the place it issues most, beginning with endpoints and progressing to taking management of identities and privileged entry credentials. Gaps in legacy tech stacks, lengthy recognized internally inside organizations however not a precedence to repair, are simply as a lot accountable because the rising sophistication of social engineering strategies, together with the rising reputation of pretexting that attackers use to defraud victims.
Attackers know that IT groups battle to get cloud configuration proper, typically leaving total situations and accounts open. IoT is one other hassle spot; distant entry opened the door to 1000’s of organizations getting hacked globally.
The Zero Belief Edge (ZTE) design targets middle on offering tech stack consolidation, decreasing dangers and prices and growing visibility and management throughout IT infrastructures. ZTE is gaining adoption with CISOs whose highest precedence, in lots of circumstances, is to consolidate from too many distributors whereas growing efficacy and strengthening safety postures. The purpose CISOs are after is to trim again the variety of firmware- and hardware-based legacy methods they’ve, along with software-defined extensive space networking (SD-WAN), safe internet gateway (SWG) and cloud entry safety dealer (CASB) distributors right into a extra built-in, adaptive structure supported by a core set of distributors.
Defining Zero Belief Edge
Forrester defines ZTE as “an answer that mixes safety and networking functionalities — comparable to software-defined WAN (SD-WAN), cloud entry safety dealer (CASB), Zero Belief community entry (ZTNA), and safe internet gateway (SWG) — {that a} single vendor can ship and assist in any mixture of cloud, software program, or {hardware} elements.” Main use circumstances embrace enhancing utility efficiency, cloud safe entry, visibility, and cloud administration require built-in networking and safety.
Forrester’s analysts write, “ZTE is a disruptive and high-stakes structure,” referring to ZTE’s means to unravel a number of important issues whereas concurrently consolidating 4 core applied sciences right into a unified structure resolution.
Early ZTE pilots are exhibiting sturdy ends in securing distant workforces, enhancing distant website safety and dependability via a number of connectivity choices, streamlining networking and offering extra streamlined safety administration. CISOs and their groups working pilots say that transitioning ZTE’s discrete elements to cloud-based managed and monitored providers helps unencumber localized {hardware} and system to optimize workloads additional domestically.

ZTE is the income engine cybersecurity distributors want
ZTE presents a big alternative for cybersecurity distributors to drive new income progress by promoting tech stack consolidation. CISOs inform VentureBeat that legacy community safety approaches have did not adequately safe immediately’s distributed environments with distant staff and cloud-based assets. One CISO confided to VentureBeat that legacy perimeter methods are similar to not having a system put in in any respect as a result of it’s past the purpose of stopping assaults invented lower than a yr in the past.
Legacy community approaches have created gaps in organizations’ means to safe assets, frequently enhance effectivity and sustain with the velocity required to capitalize on new digital enterprise initiatives. ZTE focuses on these challenges by converging safety and networking instruments into built-in, cloud-delivered structure.
In accordance with Forrester’s ZTE analysis, prime distributors are capitalizing on ZTE’s potential to consolidate level options right into a single providing consumed as a service. This aligns with CISOs’ purchaser preferences for diminished complexity and working expense (OPEX) fashions.
An estimated 78% of organizations desire to purchase or eat consolidated functionalities as a service, in line with Forrester’s Safety Survey, 2022. Forrester’s analysts observe that the highest distributors are formidable concerning their plans to supply a whole turnkey package deal, including that “the thought of getting a single structure for all safety options on an opex foundation might be compelling for the SMB/midmarket.” Forrester cautions that distributors providing ZTE are nonetheless overcoming limitations of their core areas.
With tech stack consolidation a precedence for CISOs, ZTE exhibits potential to be the following viable evolution of safety infrastructure. CISOs working pilots inform VentureBeat that ZTE is delivering measurable positive factors in operations efficiency, simpler endpoint and id safety and decrease prices because of standardizing on a unified structure. The market dynamics clarify that ZTE is the brand new income engine cybersecurity distributors want.
High ZTE use circumstances
Forrester recognized the six core use circumstances the place ZTE delivers probably the most worth. Underscoring all of them is a robust concentrate on reaching higher cyber-resilience whereas enhancing community efficiency and reliability.
CISOs from banking and monetary providers inform VentureBeat that ZTE’s use case of delivering cloud-secure entry and securing digital work groups utilizing Zero Belief Community Entry (ZTNA) is part of their pilots immediately. Each pilot VentureBeat has realized about is working real-time visibility and historical past community statistics to quantify visibility and observability positive factors.

Along with the core use circumstances, Forrester recognized 4 prolonged Zero Belief Edge use circumstances which can be much less sought by CISOs however show key vendor differentiation. Finish-to-end management offers visibility and governance throughout all community segments. Credential mapping unifies consumer identities throughout methods to simplify entry coverage enforcement. Unauthorized entry detection and prevention defend towards credential misuse and insider threats. Net content material filtering from distant websites extends acceptable use insurance policies.

Zero Belief Edge poised for progress
ZTE represents a pivotal shift in how enterprises safe their digital groups and distant staff, property, cloud environments and rising IoT networks. CISOs inform VentureBeat that legacy approaches to community, system, endpoint and id safety can’t sustain with the velocity and complexity of cyberattacks. By converging networking and safety, ZTE delivers a cloud-centric mannequin that may be consumed as a service and paid for as an working expense.
The number of scope and approaches the 22 ZTE distributors talked about on this report are taking to promote consolidation on their platforms exhibits how various the enterprise wants every is attempting to fulfill. VentureBeat has realized that preliminary ZTE pilots are assembly expectations by supporting new digital-first income initiatives whereas closing the gaps in tech stacks that led to intrusion and breach assaults up to now.
Within the close to time period, Forrester predicts bigger enterprises will take a multivendor method, integrating best-of-breed ZTE elements from market leaders talked about of their report. The core of ZTE’s simplification and consolidation worth proposition makes it a compelling technique for SMBs and midsize corporations desirous to standardize on a unified structure. Demand is rising for an answer that may remedy probably the most difficult multicloud and hybrid cloud safety challenges, assist distant work and nil belief initiatives. ZTE is properly positioned to capitalize on these market dynamics.