Be part of prime executives in San Francisco on July 11-12, to listen to how leaders are integrating and optimizing AI investments for achievement. Be taught Extra
Attackers are doubling down on backdoor assaults that ship ransomware and malware, proving that companies want zero belief to safe their endpoints and identities.
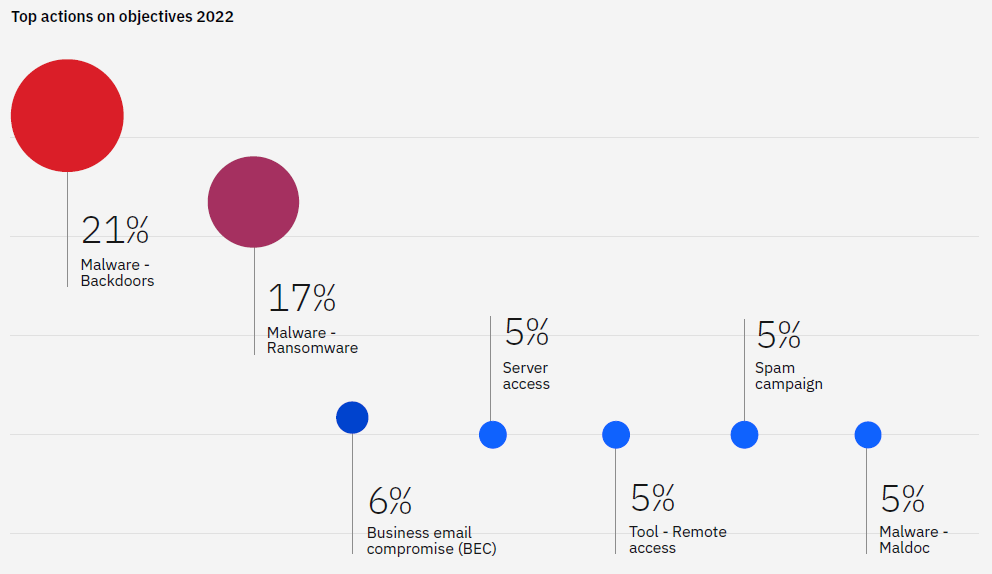
IBM’s safety X-force menace intelligence index 2023 warns that attackers are prioritizing these backdoor assaults as they try and extort downstream victims whose knowledge has been compromised. Twenty-one % of all intrusion assaults began with a backdoor breach try. Two-thirds of backdoor makes an attempt included a ransomware ingredient.
IBM’s X-Pressure Intelligence workforce additionally found that backdoor assaults surged in February and March of final yr, measured by a big spike in Emotet malware incidents. The spike was so vital that it accounted for 47% of all backdoor intrusion makes an attempt recognized worldwide in 2022.
“Whereas extortion has largely been related to ransomware, extortion campaigns have additionally included quite a lot of different strategies to use stress on their targets,” stated Chris Caridi, cyber menace analyst for IBM safety menace intelligence. “And these embrace issues like DDoS assaults, encrypting knowledge, and extra just lately, some double and triple extortion threats combining a number of of the beforehand seen components.”
Occasion
Rework 2023
Be part of us in San Francisco on July 11-12, the place prime executives will share how they’ve built-in and optimized AI investments for achievement and averted frequent pitfalls.
Register Now
Ransomware attackers are out-innovating companies that depend on perimeter-based safety. In two years, they’ve achieved a 94% discount within the common time to deploy a ransomware assault. What took ransomware attackers two months to perform in 2019 took slightly below 4 days in 2021.

The profitable world of backdoor assaults
Backdoor entry to an enterprise’s infrastructure is among the many most marketable and high-priced belongings on the market on the darkish net.
CrowdStrike’s 2023 world menace report discovered that entry brokers proceed to create a thriving enterprise remarketing stolen credentials and identities to ransomware attackers in bulk. CrowdStrike’s extremely regarded intelligence workforce discovered that authorities, monetary companies, industrial and engineering organizations had the best common asking worth for entry. Entry to the tutorial sector had a mean worth of $3,827, whereas entry to the federal government sector had a mean worth of $6,151.
The IBM workforce notes within the 2023 index that “preliminary entry brokers usually try and public sale their accesses, which X-Pressure has seen at $5,000 to $10,000, although remaining costs could also be much less. Others have reported accesses promoting for $2,000 to $4,000, with one reaching $50,000.”
Manufacturing extends its lead as probably the most attacked trade
Practically one in 4 incidents that IBM tracked in its menace intelligence index focused manufacturing, an trade identified for a really low tolerance for downtime. This will increase their motivation to pay ransomware calls for quick, and sometimes at excessive multiples.
The sector has additionally earned a popularity as a smooth goal as a result of many producers underspend on safety. Producers’ methods are down for a mean of 5 days after a cyberattack. Of those, 50% reply to the outage in three days, and solely 15% reply in a day or much less.

How organizations can battle backdoor assaults with zero belief
Backdoor assaults prey on the false sense of safety that perimeter-based methods create and perpetuate. Edward Snowden’s e book Everlasting File eliminated any doubts throughout the cybersecurity neighborhood that assumed belief is deadly. It proved that an excessive amount of belief might compromise an intelligence community. CISOs inform VentureBeat that they make a copy of this e book of their places of work and quote from it when their zero belief safety budgets are questioned.
Listed here are the confirmed methods companies can battle again towards backdoor assaults, beginning with treating each new endpoint and id as a brand new safety perimeter.
Audit entry privileges, delete pointless or out of date accounts and re-evaluate admin rights
Ivanti’s 2023 cybersecurity standing report discovered that 45% of enterprises imagine former workers and contractors nonetheless have energetic entry to firm methods and recordsdata as a consequence of inconsistent or nonexistent procedures for canceling entry. De-provisioning isn’t usually adopted, and third-party apps nonetheless have entry embedded inside them.
“Massive organizations usually fail to account for the massive ecosystem of apps, platforms and third-party companies that grant entry nicely previous an worker’s termination,” stated Srinivas Mukkamala, chief product officer at Ivanti. “We name these zombie credentials, and a surprisingly giant variety of safety professionals — and even leadership-level executives — nonetheless have entry to former employers’ methods and knowledge.”
Multifactor authentication could be a fast win
Forrester senior analyst Andrew Hewitt advised VentureBeat that the most effective place to begin when securing identities is “all the time round implementing multifactor authentication. This will go a good distance towards making certain that enterprise knowledge is secure. From there, it’s enrolling gadgets and sustaining a strong compliance commonplace with the unified endpoint administration (UEM) software.
Forrester additionally advises enterprises that, to excel at MFA implementations, they need to take into account including what-you-are (biometric), what-you-do (behavioral biometric) or what-you-have (token) elements to legacy what-you-know (password or PIN code) single-factor authentication implementations. It’s an space the place CISOs are getting fast zero-trust wins right this moment which might be saving tomorrow’s budgets.
Monitor all community visitors, assuming any person, id, endpoint or gadget might be compromised
As one of many core components of any zero belief technique, CISOs and their groups want to observe, scan and analyze community visitors to determine any backdoor threats earlier than they succeed. Practically each safety and knowledge occasion administration (SIEM) and cloud safety posture administration (CSPM) vendor contains monitoring as an ordinary function.
There continues to be a rise within the scope and scale of innovation within the SIEM and CPSM markets. Main SIEM suppliers embrace CrowdStrike Falcon, Fortinet, LogPoint, LogRhythm, ManageEngine, QRadar, Splunk and Trellix.
Restrict lateral motion and shrink assault surfaces with microsegmentation
One of many foundational ideas of zero belief is microsegmentation. The NIST zero belief framework mentions microsegmentation on the similar degree of significance as identity-based governance, authentication, and community and endpoint safety administration.
Airgap, AlgoSec, ColorTokens, Illumio, Prisma Cloud and Zscaler cloud platform have confirmed efficient in figuring out and thwarting intrusions and breach makes an attempt early utilizing their distinctive approaches to microsegmenting identities and networks.
Airgap’s zero-trust isolation platform is constructed on microsegmentation that defines every id’s endpoint as a separate entity after which enforces contextually related insurance policies, stopping lateral motion. AirGap’s belief wherever structure contains an autonomous coverage community that scales microsegmentation insurance policies network-wide instantly.

Monitor endpoints and make them self-healing and resilient
With the attacker’s software of alternative being Emotet malware, each endpoint must be resilient, self-healing and able to monitoring visitors in actual time. The objective should be to implement least-privileged entry by id for any useful resource requested throughout every endpoint.
The extra resilient an endpoint is, the extra doubtless it may possibly repel an assault on identities. A self-healing endpoint will shut down and validate its core parts, beginning with its OS. After patch versioning, the endpoint will mechanically reset to an optimized configuration. Absolute Software program, Akamai, CrowdStrike Falcon, Ivanti Neurons, Malwarebytes, Microsoft Defender, SentinelOne, Tanium, Pattern Micro and different distributors supply self-healing endpoints.
Endpoint platforms are innovating quickly in response to threats. The distinctive method of Absolute’s resilience platform gives IT and safety groups with real-time visibility and management and asset administration knowledge for any gadget, networked or not. The corporate has proven persistently excessive ranges of innovation.
Absolute additionally invented and launched the primary self-healing zero-trust platform for asset administration, gadget and utility management, endpoint intelligence, incident reporting, resilience and compliance. The corporate’s undeletable digital tether has confirmed efficient in monitoring and validating each PC-based endpoint’s real-time knowledge requests and transactions.
An information-driven method to patch administration may give IT a much-needed break
CIOs inform VentureBeat that their groups are stressed sufficient with out coping with gadget inventories that want patching. Because of this, patching will get pushed down the precedence checklist as IT and safety groups are too usually preventing fires.
“Endpoint administration and self-healing capabilities enable IT groups to find each gadget on their community, after which handle and safe every gadget utilizing trendy, best-practice strategies that guarantee finish customers are productive and firm sources are secure,” Srinivas Mukkamala, chief product officer at Ivanti, stated in a latest interview with VentureBeat.
Getting patch administration proper at scale takes a data-driven method. Main distributors on this space are capitalizing on the strengths of AI and machine studying (ML) to unravel the challenges of preserving 1000’s of gadgets present. Main distributors embrace Broadcom, CrowdStrike, SentinelOne, McAfee, Sophos, Pattern Micro, VMWare Carbon Black and Cybereason.
Some of the progressive approaches to patch administration is present in Ivanti’s neurons platform, which depends on AI-based bots to hunt out, determine and replace all patches throughout endpoints that must be up to date. Ivanti’s Threat-based cloud patch administration is noteworthy for the way it integrates the corporate’s vulnerability threat score (VRR) to assist safety operations middle (SOC) analysts take risk-prioritized motion. Ivanti had found the way to present service-level settlement (SLA) monitoring that additionally gives visibility into gadgets nearing SLA, enabling groups to take preemptive motion.

Zero belief doesn’t must be costly to be efficient
Backdoor assaults thrive when a company cuts its safety funds and depends on perimeter-based safety — or none in any respect, merely hoping a breach received’t occur.
Defining a zero belief framework that matches a company’s enterprise technique and targets is desk stakes. And the applied sciences and approaches concerned don’t must be costly to be efficient.