Head over to our on-demand library to view periods from VB Remodel 2023. Register Right here
This text is a part of a VB particular problem. Learn the total collection right here: The way forward for the info middle: Dealing with larger and larger calls for.
Zero belief is the digital protect information facilities have to harden towards more and more complicated, well-orchestrated information middle assaults. Attackers are getting access to information facilities utilizing stolen privileged entry credentials and IDs, trying to exfiltrate as a lot buyer information as potential.
Simply to call two examples, attackers efficiently obtained emails, passwords and different buyer information from Shanghai-based GDS Holdings Ltd. and Singapore-based ST Telemedia World Knowledge Centres, two of Asia’s largest information middle operators.
Resecurity Inc. not too long ago offered an in-depth evaluation of attackers’ methods to infiltrate information facilities, cloud service suppliers and managed service suppliers. Resecurity discovered that essentially the most susceptible risk vectors for information facilities embody buyer assist, customer support, and ticket administration assist portals operating on information middle servers. Attackers can acquire sufficient management to steal hundreds of buyer data and exfiltrate an organization’s most confidential information if not found.
Occasion
VB Remodel 2023 On-Demand
Did you miss a session from VB Remodel 2023? Register to entry the on-demand library for all of our featured periods.
Register Now
The problem for CIOs and CISOs is to ship digital shields that scale
Designing for belief should begin with the cornerstone of zero belief: the idea that the info middle has already been breached, and additional injury have to be contained and stopped instantly. That’s as a result of attackers are constantly fine-tuning their craft to search out and exploit gaps in information middle safety architectures and tech stacks. These gaps typically seem when long-standing on-premise safety platforms are prolonged to the cloud with out the proper configurations, leaving the programs susceptible to breach.
CIOs and CISOs are teaming as much as deal with the problem of fast-tracking safe entry service edge (SASE) and 0 belief community entry (ZTNA) initiatives in information facilities to harden digital shields towards additional assaults. CIOs tells VentureBeat that SASE improves enterprise safety postures by offering ZTNA at scale whereas serving to to consolidate information middle and enterprise-wide safety.
ZTNA must be on each CISO’s SASE roadmap. Gartner predicts ZTNA would be the fastest-growing community safety market section worldwide. It’s forecast to realize a 27.5% compound annual development price between 2021 and 2026, growing from $633 million to $2.1 billion worldwide.
Esmond Kane, CISO of Steward Well being, advises, “Perceive that — at its core — SASE is zero belief. We’re speaking about identification, authentication, entry management and privilege. Begin there after which construct out.”
CIOs and CISOs are seeing their roles overlap in cybersecurity, making shared possession of knowledge middle safety outcomes a should. At 19% of publicly-traded firms and 46% of personal firms, the CISO presently has the double position of CISO and CIO, in keeping with a survey of 650 safety executives printed earlier this 12 months by Hitch Companions.
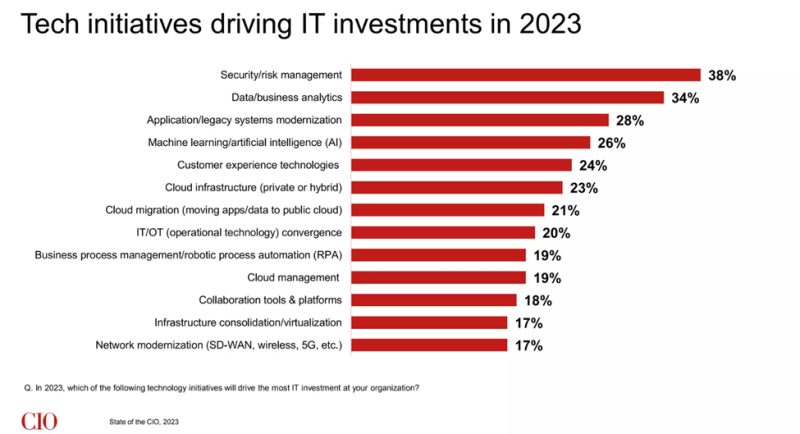
CIOs inform VentureBeat that their boards of administrators think about getting information middle safety proper to be integral to their danger administration. Eighty-eight % of boards now view cybersecurity as a enterprise danger. Foundry’s State of the CIO Research 2023 discovered that safety enhancements are essentially the most important issue driving tech price range will increase in 2023.

High 10 cybersecurity priorities for 2023
There’s no scarcity of cybersecurity weaknesses recognized to attackers, who search to take advantage of them undetected. From the unsecured networks connecting information facilities throughout a company to the legacy programs counting on perimeter-based safety, many information facilities are breaches ready to occur. Transferring workloads to the cloud typically expands the assault floor, with hybrid multicloud platforms among the many riskiest and most difficult to safe. Enterprises getting the very best outcomes base their information middle cybersecurity methods on confirmed frameworks, with SASE and ZTNA essentially the most prevalent.
1. Prioritize identification safety first, utilizing single sign-on (SSO) and multifactor authentication (MFA)
“The perfect place to start out is at all times round imposing multifactor authentication,” Forrester senior analyst Andrew Hewitt informed VentureBeat. Hewitt is the writer of the report, The Way forward for Endpoint Administration. “This may go a good distance towards guaranteeing that enterprise information is secure. From there, it’s enrolling units and sustaining a strong compliance normal with the unified endpoint administration (UEM) device,” he added.
2. Make auditing entry privileges, deleting out of date accounts and reviewing admin rights a part of the group’s muscle reminiscence
In accordance with Ivanti’s 2023 Cybersecurity Standing Report, 45% of enterprises imagine former workers and contractors nonetheless have energetic entry to firm programs and recordsdata as a consequence of inconsistent or nonexistent procedures for canceling entry. De-provisioning isn’t finished, and third-party apps nonetheless have entry. “Giant organizations typically fail to account for the large ecosystem of apps, platforms and third-party companies that grant entry properly previous an worker’s termination,” mentioned Srinivas Mukkamala, chief product officer at Ivanti.
Main IAM suppliers embody AWS Identification and Entry Administration, CrowdStrike, Delinea, Ericom, ForgeRock, Ivanti, Google Cloud Identification, IBM Cloud Identification, Microsoft Azure Energetic Listing, Palo Alto Networks and Zscaler.
3. Take into account changing legacy IAM programs that may’t monitor identities, roles and privileged entry credential exercise early in your SASE and ZTNA roadmaps
VentureBeat has realized from CISOs that legacy IAM programs lengthy used to guard networks and information facilities are having hassle maintaining with the huge numbers of latest identities being generated right now. An IAM that may observe just some identification exercise throughout roles, privileged entry credential use, and endpoint utilized in actual time is just too dangerous. Legacy IAM programs have gaps that attackers exploit by providing bounties on the darkish internet for privileged credentials to monetary companies’ central accounting and finance programs, for instance.
4. Microsegmentation can scale back information middle lateral motion and assault surfaces when a breach occurs
Succeeding with an SASE framework supported by ZTNA wants to start out with the belief that the info middle has already been breached. The objective is to cease lateral motion instantly and scale back the specter of assault surfaces resulting in a breach.
The NIST zero-trust framework prioritizes microsegmentation alongside identity-based governance, authentication, and community and endpoint safety administration. Airgap Networks, AlgoSec, ColorTokens, Illumio, Prisma Cloud and Zscaler Cloud Platform use microsegmentation to detect and cease intrusions and breach makes an attempt early.
One of the revolutionary is AirGap Networks, one of many prime 20 zero-trust startups to look at in 2023, which launched its Airgap Zero Belief Firewall, or ZTFW, earlier this 12 months. ZTFW prevents threats from spreading from IT to the core community and vice versa, even when increased community layers have been compromised. Airgap’s ZTFW defends vital enterprise infrastructure and secures core networks by offering identification, agentless microsegmentation, and safe entry for each linked endpoint.
Final month AirGap Networks acquired NetSpyGlass to allow Airgap ZTFW prospects to raised detect, find and include machine anomalies in actual time. “The larger the accuracy of asset discovery in these programs, the shorter the response time,” mentioned Ritesh Agrawal, CEO and cofounder of Airgap Networks. “With the addition of NetSpyGlass, the Airgap ZTFW presents companies the steering wheel to drive belief [in] their core community at velocity and scale. It’s a game-changer for securing business-critical networks.”
5. Actual-time asset administration throughout all endpoints and information facilities is desk stakes
CISOs use IT asset administration programs and platforms to search out and determine community gear, endpoints, associated property, and contracts. Combining bot-based asset discovery with AI and ML algorithms improves IT asset administration accuracy and monitoring.
Ivanti’s Neurons for Discovery combines bot-based asset discovery, AI and ML to create real-time service maps of community segments or a whole infrastructure. As well as, Ivanti updates configuration and asset administration databases to obtain real-time normalized {hardware} and software program stock and utilization information. Different main asset administration suppliers embody Absolute Software program, Airgap Networks, Atlassian, CrowdStrike, BMC, ManageEngine, MicroFocus and ServiceNow.
6. Actual-time telemetry information can lengthen endpoint lifecycles and catch intrusion makes an attempt that may in any other case be missed
Endpoint safety requires real-time endpoint telemetry information to detect intrusions and breaches. This information can also be useful in figuring out each endpoint’s {hardware} and software program configuration at each degree — file, course of, registry, community connection and machine information. Absolute Software program, BitDefender, CrowdStrike, Cisco, Ivanti and Microsoft Defender for Endpoint, which secures endpoint information in Microsoft Azure, and different main distributors use real-time telemetry information to generate endpoint analytics.
CrowdStrike, ThreatConnect, Deep Intuition and Orca Safety calculate IOAs and IOCs utilizing real-time telemetry. IOAs determine an attacker’s intent and targets no matter malware or exploit. IOAs and IOCs present forensics to show a community breach. Automating IOAs provides correct, real-time information to know attackers’ intent and cease intrusion makes an attempt.
CrowdStrike launched the primary AI-powered IOAs to guard endpoints utilizing real-time telemetry information. The corporate informed VentureBeat in a current briefing that AI-powered IOAs work asynchronously with sensor-based machine studying and different sensor protection layers.
7. As information middle endpoints tackle extra identities, they want audits and enhancements to essential digital certificates administration
Every community machine wants a novel identification to handle and safe machine-to-machine communications. Extra identities on endpoints make it more durable to safe all of them.
Key and digital certificates administration have to be prioritized. SSL, SSH keys, code-signing certificates, TLS, and authentication tokens assign digital identities. Cyberattackers bypass code-signed certificates or compromise SSL and TLS certificates to assault SSH keys. Knowledge middle safety groups should be sure that each machine’s identification is correct, dependable and reliable. CheckPoint, Delinea, Fortinet, IBM Safety, Ivanti, Keyfactor, Microsoft Safety, Venafi and Zscaler are main suppliers on this space.
8. Datacenter endpoints should determine an intrusion try and autonomously self-heal
CISOs inform VentureBeat they’re inheriting information facilities situated 5 or extra time zones away. Sending workers to refresh endpoints isn’t possible or financially prudent given the price range crunch many face. Many are evaluating and adopting self-healing endpoints that may seize and act on real-time telemetry information, rebuild themselves if breached, and might be programmed to brick themselves if needed.
Closing the gaps between identification administration and endpoint safety is the way forward for zero belief. Michael Sentonas, CrowdStrike’s president, informed VentureBeat in a current interview that closing the hole between identities and endpoints is “one of many largest challenges that individuals wish to grapple with right now. I imply, the hacking [demo] session that George and I did at RSA [2023] was to point out among the challenges with identification and the complexity. The rationale why we linked the endpoint with identification and the info that the consumer is accessing is as a result of it’s a vital drawback. And if you happen to can resolve that, you’ll be able to resolve a giant a part of the cyber drawback that a company has.”
Absolute Software program, Akamai, Cisco, CrowdStrike, ESET, Cybereason Protection Platform, Ivanti, Malwarebytes, Microsoft, SentinelOne, Tanium, Development Micro and lots of others distributors supply autonomously self-healing endpoints. Absolute Software program is among the many most original in that it gives an undeletable digital tether to each PC-based endpoint to watch and validate real-time information requests and transactions. Absolute’s Resilience platform routinely repairs or reinstalls mission-critical functions and distant queries, remediating distant units at scale. The platform may also uncover delicate information on endpoints and examine and get well stolen units. Absolute additionally turned its endpoint experience into the business’s first self-healing zero-trust platform.
9. Deploy risk-based conditional entry for each information middle risk floor, beginning with endpoints
Danger-based entry for functions, endpoints and programs is enabled in least-privileged entry periods primarily based on machine kind, settings, location and anomalous behaviors. Actual-time danger scores are calculated by cybersecurity distributors utilizing ML algorithms. “This ensures MFA (multifactor authentication) is triggered solely when danger ranges change — guaranteeing safety with out lack of consumer productiveness,” CrowdStrike’s Raina informed VentureBeat. Main distributors offering risk-based conditional entry embody CheckPoint, CrowdStrike, Fortinet, IBM Safety, Ivanti, Microsoft Safety, Venafi and Zscaler.
10. Knowledge-driven, automated patch administration reduces IT staff workload
CIOs inform VentureBeat that their IT groups are too overwhelmed with initiatives and pressing requests to work by the stock of units that want updates. An information-driven strategy is required for large-scale patch administration.
Main banking, monetary companies and manufacturing firms, and CIOs and CISOs who run a number of information facilities, are adopting AI- and ML-based programs to maintain the hundreds of units throughout their information facilities up to date. Main distributors embody Broadcom, CrowdStrike, Ivanti, SentinelOne, McAfee, Sophos, Development Micro, VMWare Carbon Black and Cybereason.
Ivanti’s Neurons platform makes use of AI-based bots to search out, determine and replace all endpoint patches. Ivanti’s risk-based cloud patch administration integrates the corporate’s vulnerability danger score (VRR) to assist SOC analysts prioritize danger. Ivanti found the way to observe service-level agreements (SLAs) and alert groups to units nearing SLAs.

Knowledge middle cybersecurity is a enterprise determination
CIOs and CISOs have to companion to outline a unified cybersecurity technique to guard information facilities, lots of that are being protected with legacy perimeter-based programs right now. Selecting an SASE-based technique with ZTNA at its core is the path many banking, insurance coverage and monetary companies enterprises are going right now. This strategy is properly fitted to monetary companies, for instance, which should maintain sure programs on-premises for compliance necessities.
Attackers transfer quicker than essentially the most environment friendly IT, cybersecurity and SecOps groups do right now. To guard their information facilities, CIOs, CISOs and their groups should begin by defending identities first. The ten priorities above are a roadmap to get began making a hardened digital protect that may scale back breaches and alleviate their severity. Breaches are coming; it’s a matter of minimizing the blast radius and lowering the losses they’ll create.