Take a look at all of the on-demand classes from the Clever Safety Summit right here.
A talented attacker can scan and discover unprotected endpoints on an enterprise community in seconds, taking only one hour and 24 minutes to maneuver from the preliminary level of compromise to different programs. That’s 14 minutes quicker than final 12 months, based mostly on Falcon OverWatch’s findings within the 2022 CrowdStrike International Menace Report.
Over-configured endpoints are simply as weak, creating risk surfaces as they decay. A typical endpoint has, on common, 11.7 safety controls put in, and every is decaying at a unique charge. Absolute Software program’s Endpoint Danger Report discovered that 52% of endpoints have put in three or extra endpoint administration purchasers, and 59% have put in at the very least one identification entry administration (IAM) shopper.
Unprotected and overprotected endpoints not managed properly are a breach ready to occur. Endpoint intrusions typically result in months-long breaches costing tens of millions of {dollars}. The Ponemon Institute and Adaptiva’s 2022 report, Managing Dangers and Prices At The Edge, discovered that 54% of organizations have had a mean of 5 assaults on their endpoints previously 12 months. The annual price of those annual assaults is $1.8 million, or $360,000 per assault.
Solely 20% of CISOs and cybersecurity leaders say they may stop a dangerous breach at this time, regardless of 97% believing their enterprises are as ready or extra ready for a cyberattack than a 12 months in the past. Ivanti’s State of Safety Preparedness 2023 Report displays enterprises’ pressing have to upscale their tech stacks, consolidating purposes to enhance efficiency whereas decreasing prices.
Occasion
Clever Safety Summit On-Demand
Be taught the important position of AI & ML in cybersecurity and trade particular case research. Watch on-demand classes at this time.
Watch Right here
What’s driving extra spending on endpoint safety
CISOs cope with a threatscape the place endpoint sprawl creates extra human and machine identities than many enterprise safety groups can monitor and defend. The standard enterprise reviews having greater than 250,000 machine identities. It’s no shock that in lots of enterprises, machine identities outnumber human identities by 45 occasions.
Cybercriminal gangs are more and more utilizing synthetic intelligence (AI) and machine studying (ML) to go on the offensive. Essential targets for these applied sciences are figuring out unprotected, weak endpoints in milliseconds, inventing new methods to evade detection so malware could be put in on enterprise servers, and automating phishing assaults, whereas additionally performing ongoing community reconnaissance.
“Safety consultants have famous that AI-generated phishing emails have larger charges of being opened — [for example] tricking potential victims into clicking on them and thus producing assaults — than manually crafted phishing emails,” stated Brian Finch, co-leader of the cybersecurity, information safety and privateness observe at legislation agency Pillsbury Regulation. “AI will also be used to design malware that’s always altering, to keep away from detection by automated defensive instruments.”
The mixture of offensive AI strategies which can be practically unattainable to establish and cease with legacy endpoint programs mixed with the necessity to replace tech stacks to zero belief are driving spending. CISOs inform VentureBeat that they’re counting on zero-trust wins they’ll rapidly obtain to avoid wasting subsequent 12 months’s funds. Ivanti’s research validates that cybersecurity budgets are rising subsequent 12 months, discovering that 71% of CISOs and safety professionals predict their budgets will leap a mean of 11%.
Gartner’s forecast is equally optimistic, predicting worldwide spending on info safety and danger administration will develop from $157.7 billion in 2021 to $261.5 billion in 2026, attaining a compound annual progress charge (CAGR) of 11.1%.
Endpoint safety platform spending worldwide is projected to extend from $11.9 billion in 2021 to $25.8 billion in 2026, greater than doubling in dimension in 5 years. Frost and Sullivan’s Endpoint Safety Forecast predicts that the worldwide endpoint safety market will attain $31.1 billion by 2026, up from $17.4 billion in 2021, attaining a 12.3% CAGR.
Evaluating main endpoint safety distributors
CISOs want endpoint safety suppliers to go on the offensive and supply cloud-based platforms able to decoding and taking motion on a broader base of telemetry information in real-time. CrowdStrike’s 2022 Falcon OverWatch Menace Looking Report found that 71% of all detections listed by the CrowdStrike Menace Graph are malware-free intrusions.
“A key discovering from the report was that upwards of 60% of interactive intrusions noticed by OverWatch concerned the usage of legitimate credentials, which proceed to be abused by adversaries to facilitate preliminary entry and lateral motion,” stated Param Singh, VP of Falcon OverWatch at CrowdStrike.
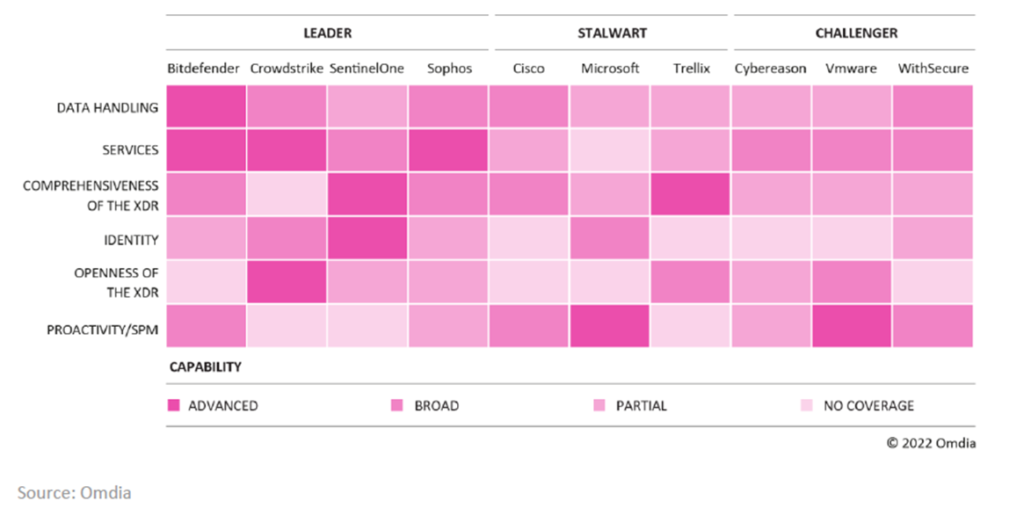
The Omdia Market Radar: Endpoint Safety Platforms 2022 report seems to be at six core areas of endpoint safety platform efficiency. These measure how properly an endpoint platform will scale and meet the 4 core areas of stopping and defending in opposition to file-based and file-less malware exploits; permitting or blocking processes, scripts and software program; detecting and stopping threats utilizing behavioral evaluation; and instruments to research incidents and outline remediation methods.
Omdia’s evaluation discovered that Bitdefender, Cisco, CrowdStrike, Microsoft, SentinelOne, Sophos and Trellix are the highest-performing endpoint suppliers available on the market. Absolute Software program, Morphisec and Pattern Micro are distributors to observe.
“Cyberthreats and compliance challenges have accelerated alongside explosive progress in distant work, creating new challenges for enterprises which can be attempting to mitigate the heightened danger that conventional safety instruments can now not tackle,” stated Rik Turner, principal analyst for cybersecurity at Omdia. “This new Radar identifies the newest improvements that successfully defend fashionable enterprise edge environments with out disrupting enterprise operations. As a result of all organizations have distinctive necessities, we profiled further distributors delivering extremely differentiated capabilities to the market.”

Evaluating distributors’ strengths and weaknesses
Bitdefender, Cisco, CrowdStrike, Microsoft, SentinelOne, Sophos and Trellix are confirmed enterprise-grade endpoint safety platforms that contribute to zero-trust initiatives at this time. Absolute Software program, Morphisec, and Pattern Micro even have confirmed their platforms enterprise-ready throughout a broad spectrum of firms and use instances. Omdia’s conclusion that these three endpoint platform suppliers are those to observe displays what VentureBeat hears from CISOs with expertise on these platforms.
Bitdefender excels at Lively Listing integration, and dashboards have greater than sufficient choices
Bitdefender clients inform VentureBeat that integrating with Lively Listing is without doubt one of the platform’s strongest options, together with stable efficiency managing passwords, keys and insurance policies. Customers additionally say that Bitdefender’s GravityZone Electronic mail Safety helps cease phishing assaults.
Weaknesses embrace having too many choices to configure dashboards with, which one CISO advised VentureBeat tempts safety groups to “boil the secops ocean” given what number of choices there are. Prospects additionally say Home windows assist is essentially the most complete, with Linux and macOS needing an equitable quantity of assist.
Cisco Safe Endpoint will get larger consumer marks for its scalability and risk detection, whereas scanning must be improved
Cisco’s clients respect how properly Safe Endpoint is built-in into the broader Cisco Safety Suite. Prospects additionally reward Cisco’s strategy to cloud companies and secured endpoints, ThreadGrid integration and well-designed dashboards. Customers even have excessive regard for Cisco Safe Endpoint and Cisco Talos, which offer real-time risk intelligence that helps detect new threats and malware.
Customers need to see Cisco transfer quicker to mature their endpoint and detection response (EDR) programs and broader stack and do extra to scale back false positives the system creates. One other buyer grievance is how a lot reminiscence endpoint brokers can take if not optimally configured and the way scanning generally produces false positives.
CrowdStrike’s many strengths have attracted essentially the most enthusiastic buyer base in endpoint safety, with Indicators of Compromise (IOC) being an space they need extra coaching on
VentureBeat has spoken with greater than a dozen CrowdStrike clients this 12 months and located that their favourite options of the CrowdStrike Falcon platform embrace how straightforward it’s to deploy customers’ machines, how briskly and responsive the corporate’s EDR assist groups are, and the way its cloud console manageability delivers stable, reliable outcomes. Prospects additionally suggest behavioral evaluation of gadgets, real-time risk detection, and customised dashboards.
Prospects need extra steering on configuring Indicators of Compromise (IOC). One buyer advised VentureBeat that putting in Falcon in advanced enterprise networks requires technical experience from CrowdStrike’s devoted account staff.
Microsoft Defender for Endpoint will get excessive reward for stable antivirus, malware and risk safety, with customers asking for improved vulnerability reporting
Defender for Endpoint customers advised VentureBeat that they think about Microsoft’s endpoint safety answer the very best for combating malware, ransomware and spy ware threats. For instance, they’ve seen Defender for Endpoint cease breach makes an attempt embedded in unrecognizable .exe information. They’re additionally seeing how efficient utility management, exploit safety, hardware-based isolation, community safety, internet safety and community firewall assist is.
The commonest grievance from Defender from Endpoint is how the mixing for remediation and patch administration is much less superior than different platform areas.
SentinelOne Singularity Platform is without doubt one of the most extremely regarded in endpoint safety, but clients complain about persistence of endpoints
VentureBeat spoke with a number of SentinelOne clients who changed on-premises programs with SentinelOne to realize higher detection and cloud administration, and extra visibility and management throughout enterprise-scale threatscapes. Prospects inform VentureBeat that the deployment went easily, and the groups from SentinelOne helped outline the very best configuration given their funds constraints.
A typical buyer grievance is that the scanning engine could be difficult to configure for optimum efficiency, resulting in too many false positives. Prospects say this results in many threats being labeled ambiguously, making analysts’ duties within the safety operations facilities (SOC) more difficult.
Sophos Intercept X is very regarded for its use of ML to detect malware, but it wants to enhance scanning alert accuracy
Prospects inform VentureBeat that Sophos Intercept X excels at utilizing ML to detect malware and prioritize essentially the most pressing threats. Sophos XDR built-in rapidly with cloud, community and server infrastructure — together with cellular and electronic mail programs — all in a single platform, which improves accuracy. Prospects additionally reward a crypto guard characteristic that permits reversing the encryption of unauthorized information, stopping attackers from publishing an organization’s info for ransom.
Like different endpoint platforms, clients say Sophos wants to enhance the extent of customization for scanning and supply higher management over disk utilization of the scan, together with extra management over asset administration on the endpoint stage.
Trellix Endpoint Safety is acknowledged as a stable built-in suite, but endpoints aren’t configured to self-heal
Recognized for having a well-integrated suite of endpoint safety instruments, Trellix is a market chief within the endpoint safety market, Their integration of asset administration, utility management, endpoint intelligence, behavioral evaluation and automatic remediation are thought of among the many finest within the trade. Their cloud portal helps and streamlines utilizing multifactor authentication (MFA) on an enterprise scale.
Weaknesses embrace too many false positives if scanning is just not optimized for a given company setting, and challenges getting the platform built-in with legacy safety info and occasion administration (SIEM) platforms. Prospects additionally inform VentureBeat that their endpoints should not as self-healing as they’d hoped and want to see that improved.
Evaluating Omdia’s firms to observe
Absolute Software program
Absolute’s Resilience platform gives real-time visibility and management of any gadget on a community or not, together with detailed asset administration information. It’s additionally the trade’s first self-healing zero-trust platform that gives asset administration, gadget and utility management, endpoint intelligence, incident reporting, resilience and compliance.
What’s additionally noteworthy about Absolute is how they’ve collaborated with 28 gadget producers who’ve embedded Absolute firmware of their gadgets to allow an undeletable digital tether to each gadget to assist guarantee the very best ranges of resiliency. Omdia notes how profitable Absolute’s partnerships proceed to be, with main gadget producers embedding its patented Persistence expertise into their gadgets’ firmware. In keeping with the Omdia evaluation, the corporate is embedded in over half a billion laptops. It presents three product traces: Safe Endpoint, Safe Entry and Utility Persistence-as-a-Service.
The Safe Endpoint product portfolio permits IT and safety personnel to observe and tackle laptop computer pc issues and permits the laptops and their mission-critical purposes to self-heal. This helps with IT administration, strengthening an organization’s safety posture, and sustaining compliance. The corporate presents three tiered Safe Endpoint choices: Absolute Visibility, Absolute Management and Absolute Resilience.
All three tiers are managed from a cloud-based, configurable dashboard with predefined and customized reviews and alerts. It may be built-in with ServiceNow and third-party SIEM instruments. Absolute Insights for Endpoints, an add-on module for anomaly detection utilizing real-time and historic information throughout gadgets, can be out there as an choice for any tier.
Omdia notes that Absolute launched Absolute Ransomware Response in April 2022, which repackages its Absolute Resilience providing with further restoration companies centered on assessing ransomware preparedness and response. That is additionally supplied as an add-on to Absolute Visibility or Absolute Management, however is just out there for Home windows gadgets in all instances. All Safe Endpoint options make the most of the patented Absolute Persistence expertise.
In November 2021, Absolute launched a brand new product line referred to as Utility Persistence-as-a-Service (APaaS), enabling impartial software program distributors (ISVs) to embed Absolute’s self-healing utility capabilities into their safety and enterprise purposes — serving to guarantee they keep put in, wholesome and dealing throughout their whole buyer base. Absolute’s path to market follows a “land and broaden” strategy, utilizing channel companions on the outset and increasing by way of its direct gross sales pressure to broaden or renew.
Absolute additionally has its Safe Entry portfolio, which was added by way of the acquisition of NetMotion in Might 2021, and includes Absolute VPN, which is an enterprise VPN; Absolute ZTNA, which gives a software-defined perimeter with entry insurance policies outlined on the endpoint; and Absolute Insights for Community, which has diagnostics and expertise monitoring throughout endpoints and community.
Morphisec
Morphisec is a cybersecurity firm that provides endpoint safety options by way of its Shifting Goal Protection (MTD) expertise. MTD works by always altering the real-time reminiscence construction of an utility unpredictably, making it tough for attackers to inject code and perform assaults. Morphisec’s expertise can defend in opposition to varied assaults, together with polymorphic, file-less, APT and ransomware.
The corporate presents Home windows and Linux working programs merchandise and could be built-in with different endpoint safety and EDR platforms.
Morphisec’s expertise has minimal impression on system efficiency and could be deployed with out requiring a system restart. The corporate plans to launch variations for containers and serverless environments.
Omdia notes that, whereas it’s within the endpoint safety market, Morphisec presents neither an EPP nor an EDR platform. Relatively, it enhances and augments both of some of these platforms. Its expertise providing is engaging as a result of it doesn’t depend on prior data, in contrast to the signatures that historically underpin EPPs and the behavioral evaluation utilized by EDR, since regular habits should be modeled beforehand to detect anomalies.
As a substitute, it seeks to scale back a company’s assault floor through the use of what it calls Shifting Goal Protection (MTD), which is a method of delivering the proactive safety that Omdia has been highlighting as a rising pattern out there over latest months.
Morphisec has launched a model of its MTD expertise for Linux working programs referred to as Morphisec Knight, particularly designed to guard in opposition to refined assaults which have grow to be extra prevalent on the Linux platform. Morphisec Knight presents runtime exploit prevention and assault floor discount for legacy or unprotected programs, with minimal impression on system efficiency. It’s the solely answer that may block most supply-chain assault variations in actual time with out prior data, addressing a typical downside within the cybersecurity trade.
The Linux model of the expertise operates in a different way than the model for Home windows, utilizing an agent within the kernel to vary the system’s functioning in order that solely trusted apps have entry. A container model is deliberate for launch later this 12 months, with a model for serverless environments deliberate for 2023.
As of mid-2022, Morphisec supplied its cloud-based cybersecurity expertise to greater than 5,000 firms throughout 8.7 million endpoints by way of a software-as-a-service (SaaS) mannequin and on-premises deployment. The corporate costs on a per-server/endpoint/digital machine/digital desktop foundation.
The corporate has raised a complete of $50 million in funding, with its most up-to-date $31 million sequence C in March 2021, led by Jerusalem Enterprise Companions with participation from present buyers Orange Ventures, Deutsche Telekom Capital Companions and OurCrowd.
Pattern Micro
Pattern Micro is a well-established firm within the endpoint safety market, has been a major participant within the endpoint safety platform (EPP) house, and is without doubt one of the first distributors to broaden into EDR. Nonetheless, Omdia included it as a vendor to observe as a result of its product providing is present process important adjustments, making it unfair to match its present product to these of different distributors.
Omdia notes that Pattern Micro is consolidating its endpoint, server and cloud workload safety applied sciences onto a single platform referred to as Cloud One. This platform already delivers all the firm’s cloud safety applied sciences, resembling workload safety, safety posture administration and software program composition evaluation, by way of a partnership with Snyk.
The transfer to Cloud One will permit for higher scalability, enabling the platform to deal with giant quantities of telemetry from present and future endpoint programs. Whereas Pattern’s present endpoint safety product, Apex One, has each on-premises and SaaS variations, the latter lacks the scalability of the brand new Cloud One platform.
Pattern Micro plans to step by step roll out its new endpoint safety providing, the Endpoint Safety Service, to keep away from disruption for present Apex One clients. The brand new providing would be the subsequent model of the corporate’s endpoint safety expertise, with enhanced consumer interface and workflows, improved efficiency and consolidated capabilities throughout endpoint, server and workload safety.
What’s in retailer for 2023
Endpoint safety platforms have to speed up product growth and R&D to maintain up with an more and more deadly threatscape. Distributors have to comply with CrowdStrike’s and Ivanti’s lead on integrating AI and ML into their core platforms, utilizing each applied sciences to defend in opposition to attackers and attempting to innovate with these applied sciences rapidly.
Secondly, it’s clear that the cloud has gained the endpoint safety market and can proceed to be a core a part of any future product technique. Thirdly, there will likely be a higher concentrate on consumer habits and danger administration to assist higher establish and take motion on threats in 2023.
Additionally, the core components of a zero-trust framework will grow to be extra compliant throughout the greater than 100 totally different endpoint safety platforms out there at this time. Lastly, information safety and privateness will outline how endpoint safety suppliers meet compliance, regulatory and buyer necessities.
“Endpoint administration and self-healing capabilities permit IT groups to find each gadget on their community, after which handle and safe every gadget utilizing fashionable, best-practice strategies that guarantee finish customers are productive and firm sources are protected,” Srinivas Mukkamala, chief product officer at Ivanti advised VentureBeat.
“Automation and self-healing enhance worker productiveness, simplify gadget administration and enhance safety posture by offering full visibility into a company’s whole asset property and delivering automation throughout a broad vary of gadgets.”