We’ve come a good distance since 1993, when Peter Steiner’s now-infamous and oft-cited ‘On the Web, no person is aware of you’re a canine’ cartoon hit the pages of The New Yorker.
Nowadays, nonetheless, there are most likely fairly a couple of individuals on the Web who’ll have a good suggestion when you’re a canine. They most likely additionally know, or might simply discover out, your title, what you appear like, the place you reside, the place you’re employed, your date of delivery, the title of the primary faculty you went to, and perhaps your mom’s maiden title as properly.
If that sounds horrifying, then maybe it needs to be – id fraud accounted for 68% of circumstances filed to the Nationwide Fraud Database in 2022, and the vast majority of these circumstances (86%) resulted from on-line interactions, in keeping with Cifas, a cross-industry UK fraud prevention service.
If somebody does handle to piece sufficient info collectively about you, they’ll open financial institution accounts in your title and use them for cash laundering, apply for loans and extra. You’ll then be chased to pay again these loans, and the police would possibly assume you are the one chargeable for cash laundering. Sorting this out and proving it wasn’t you possibly can take time, contain lots of stress and will even price you your job. Id theft can break your life, so defending your id needs to be a high precedence.
And it isn’t simply fraudsters who is perhaps after your info. Being lax about privateness and safety on-line means you may inadvertently arm nearly anybody with details about your pursuits and whereabouts, from that one that used to terrorise you in school who now retains attempting so as to add you on Fb, to a vindictive ex-partner, or that terrible fleeting acquaintance who retains attempting to get you to endorse them on LinkedIn (when you’re studying this, please go away me alone).
Thankfully there are quite a lot of instruments at your disposal to assist higher shield your on-line id, in addition to adopting some greatest practices and taking proactive steps. Listed here are the primary ones you need to learn about – and put into motion!
1. Use a password supervisor
A method individuals can get to your private info is by guessing your passwords and logging into accounts that include that info.
Sustaining separate passwords for each account you utilize is a drag, to not point out impractical.
You might give you sturdy and distinctive passwords for the whole lot that requires one, and perhaps even write these down on a chunk of paper, or in a pocket book, and preserve that someplace secure. That, clearly, isn’t handy for instances whenever you’re out and about.
You can in concept take that pocket book with you, however, in fact, when you lose your pocket book, then you definitely’ve received to reset passwords for the whole lot and begin once more. If it’s stolen, then, properly, you’ve simply given whoever’s stolen it a veritable goldmine of knowledge.
You can additionally use a third-party service resembling Fb or Google to signal into different apps and providers – a extra handy answer, however then, in fact, you’re giving Fb and Google, or whoever, a fair better concept of your looking and spending habits.
A extra sensible choice is to make use of a password supervisor, an app which shops and encrypts login particulars for each service you utilize behind a single, sturdy grasp password.

Jim Martin / Foundry
The perfect password managers can shield your accounts with biometric logins that means you need to use fingerprint scanners and front-facing cameras in your telephone, laptop computer, or PC to substantiate that it’s certainly you that’s logging in, and never another person.
A superb password supervisor may also assist multi-factor authentication by default, which implies whenever you appropriately enter your grasp password, you’ll even be required to enter an extra code, securely despatched to you thru one other app. Talking of which…
2. Use two-factor or multi-factor authentication
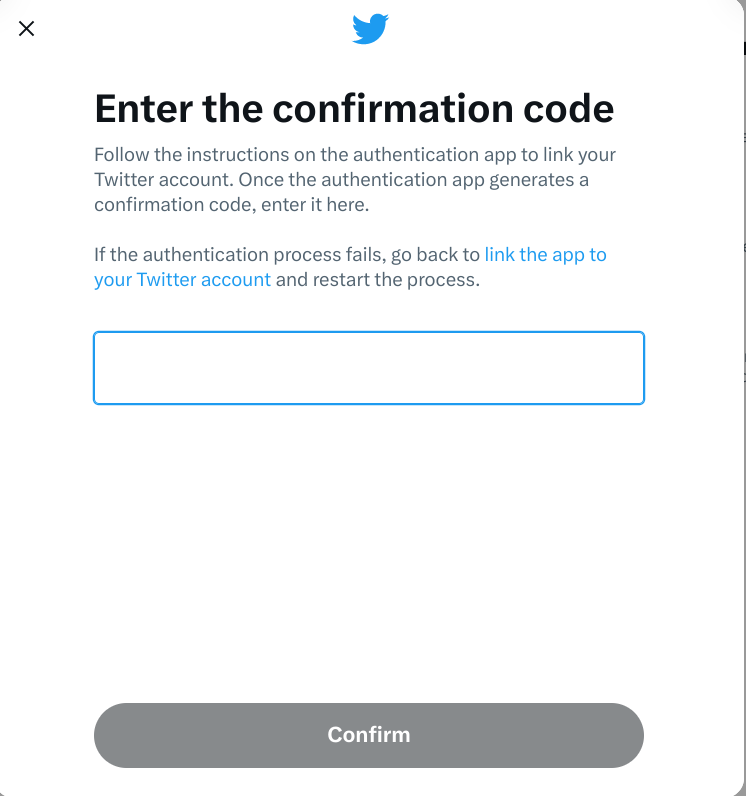
Two-factor authentication, generally expressed as ‘2FA’, or generally ‘two-step verification’, is a straightforward however efficient approach of including an additional layer of safety to any account you frequently register to.
IDG / Ashley Biancuzzo
With two-factor authentication arrange, when you’ve entered your password – the primary issue of authentication – you’ll be despatched a 4 or six digit code to enter as properly – the second issue of authentication.
If you happen to don’t have entry to that second code, then you definitely’re not getting in. Meaning it doesn’t matter if somebody has appropriately guessed your password: they nonetheless can’t entry your account.
The perfect method is to have authentication codes despatched to you by way of an authenticator app, resembling Authy, Duo Cell, Google Authenticator, or Microsoft Authenticator. Some password managers, like Dashlane and 1Password, include their very own built-in authenticators.
You can additionally take into account investing in a safety key. These {hardware} units should be plugged into one in all your laptop computer’s USB port, or tapped in your telephone to authenticate by way of NFC. It’s worthwhile to watch out to not lose them, very similar to your home keys, and so they’re not supported by all that many providers on-line.
Safety key choices embody Yubico’s YubiKey 5C, CryptoTrust’s OnlyKey, and Thetis’s FIDO2.
3. DON’T have authentication codes texted to you
Whereas 2FA is a good concept in concept, in observe, it’s not a good suggestion to have firms textual content you authentication codes.
The explanation for that is easy: SMS textual content messages may be intercepted, and it doesn’t require pricey tools or in depth technical data to take action. As soon as somebody has your authentication code, then they may very properly achieve entry to quite a lot of issues; your on-line checking account or funding portfolio, or no matter you’re attempting to log in to.
If a service helps 2FA, you need to examine if you need to use an authenticator app as an alternative having codes by way of textual content/SMS.
Alternatively, there is perhaps an choice to be despatched authentication codes by way of e-mail as an alternative. That’s a safer choice, as your e-mail supplier needs to be encrypting messages in transit as customary. Nevertheless, in case your e-mail account is compromised, then you definitely’re in danger.
Because of this, it’s good observe to robotically delete any sort of authentication e-mail that’s despatched to your account.
4. Use a VPN
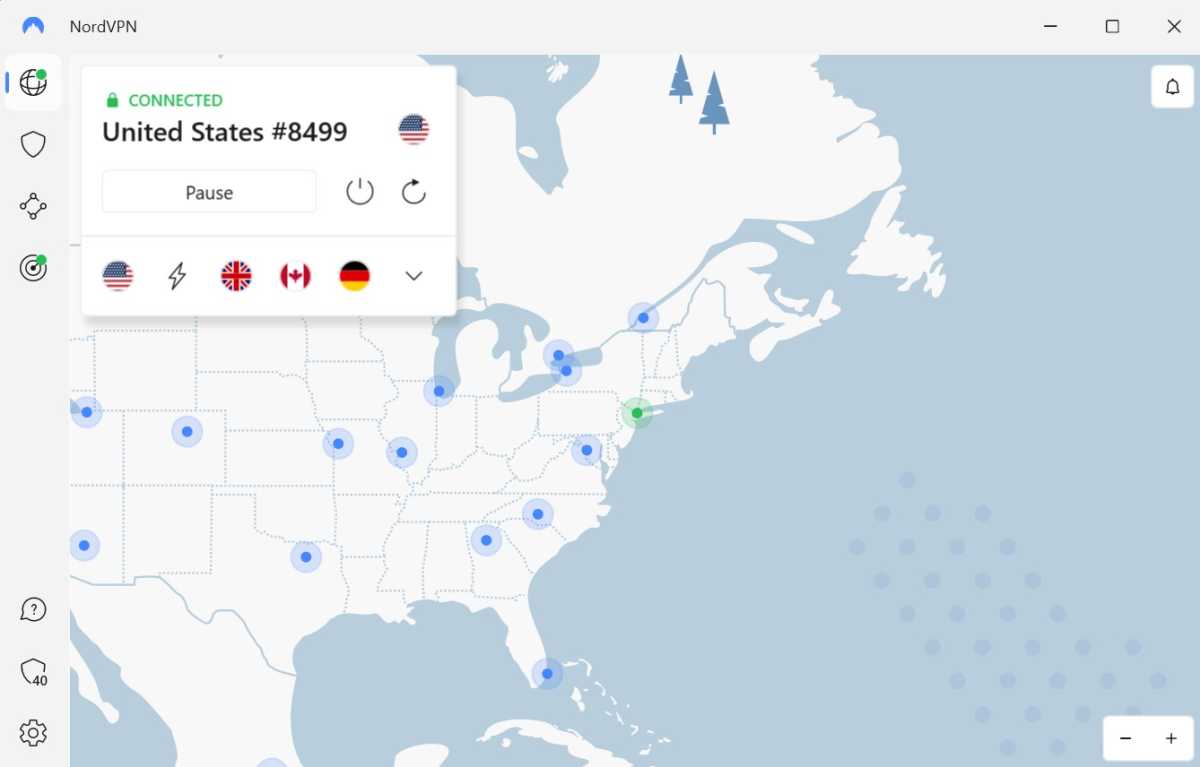
A VPN (Digital Personal Community) is an effective approach of securing your on-line exercise, as a VPN encrypts all your community site visitors, stopping anybody from retaining a log of your on-line classes.
Anyron Copeman / Foundry
Nicely, virtually anybody – the one organisation that would know which websites and providers you go to and log in to is the VPN supplier itself.
This is the reason, when buying round for a VPN supplier you will need to examine to see if the VPN supplier operates a strict ‘no connection logs’ coverage, and, extra importantly, if that coverage has been independently verified.
VPNs which have made the grade on this regard in our most up-to-date spherical of testing embody NordVPN, CyberGhost, and PureVPN – see our round-up of the perfect VPN providers for a full breakdown.
5. Use burner e-mail handle
Whereas newsletters may be nice methods of discovering out about promotions and getting some money-off vouchers, it is perhaps a good suggestion so that you can signal as much as these utilizing a devoted e-mail handle, as an alternative of your major one.
Foundry / IDG
Whereas 2-for-1 offers and low cost pizzas are nice, what’s not nice is when advertising and marketing firms share subscriber info with knowledge brokers, which might result in you being despatched lots of advertising and marketing emails for stuff you by no means even signed up for within the first place, or aren’t even curious about.
Whereas that in itself is just not an inherent safety danger, what it might do is make it more durable so that you can spot rip-off emails and related phishing makes an attempt, which regularly disguise themselves as official advertising and marketing emails. Plus, who needs unsolicited mail? No-one.
If all advertising and marketing site visitors is funneled in direction of a particular e-mail account, it leaves your mail account with emails you would possibly truly wish to learn.
6. Ask knowledge brokers to delete info they maintain on you
Information brokers, resembling Acxiom, Equifax, Experian, and TransUnion generate income from promoting details about you to advertising and marketing firms.

Tech Advisor/Foundry
Details about you possibly can come from quite a lot of sources, from firms promoting your knowledge to 3rd events as described above, from analysing your internet looking historical past, and your buying historical past.
Whereas the UK has now left the European Union, the phrases of the EU’s GDPR (Basic Information Safety Regulation) nonetheless applies.
Below Article 21 of the GDPR, you possibly can order firms to cease processing any private knowledge they maintain on you for the needs of promoting, and below Article 15, you might have the correct to make an SAR (topic entry request), the place an organization should share all and any private knowledge they maintain about you, totally free.
Within the U.S. your rights at the moment range from state to state, however you continue to could also be profitable in contacting an organization or organisation with an SAR – or SRR (topic rights request) as they’re additionally identified. U.S. primarily based non-profit Privateness Rights Clearninghouse maintains a listing of knowledge brokers, which states they’re situated in, and whether or not or not they permit an choose out.
As per the Australian Privateness Act, you possibly can request entry to the info that an organization holds on you, and request to appropriate any incorrect info, delete it or de-identify it, whether it is now not required for his or her functions.
With a purpose to make any sort of entry request, you will have to offer some primary info – resembling your title, house handle, telephone quantity e-mail handle – and presumably some supplementary info, resembling your account title/person ID, in order that an organization can appropriately establish you and course of your request.
You may as well pay third events to contact knowledge brokers in your behalf, in case you are brief on time – organisations providing such a service embody DeleteMe, Incogni, OneRep, OptOutUK, and PrivacyBee.
Nevertheless, knowledge brokers could not reply to requests made on behalf of people by third events resembling these. It is perhaps that an organization can solely let you know who holds knowledge about you – by which case it might then be as much as you to contact the corporate, and request that they delete any knowledge held on you.
7. Lock down or delete social media accounts
Along with eliminating the inevitable cringe posts and photographs of you with regrettable haircuts/outfits/each, closing or deleting outdated or inactive social accounts and blogs may be a good suggestion, particularly in the event that they include something too private.

Hannah Cowton/Foundry
Whether or not it’s damaging to your status or private credibility or not, there’s info you’ve posted on the market on a platform you’ve not up to date or maintained for quite a lot of years, there’s an opportunity that somebody might achieve entry to your profile. It’s best to purge any outdated accounts, particularly if they’re nonetheless linked to an lively e-mail handle.
Briefly, when you’re now not utilizing Fb, Twitter, Instagram, or any sort of platform, take into account deleting it, or, on the very least, lock down the privateness settings to regulate who can see that knowledge. That approach you continue to preserve a presence on these platforms, however they’re a lot much less possible for use by anybody attempting to impersonate you.
8. Don’t share an excessive amount of on-line
Comic Stewart Lee as soon as memorably described Twitter as “the Stasi for the Indignant Birds technology”, and famously doesn’t preserve a private social media presence.

Tech Advisor/Foundry
Whilst you may not wish to make use of the identical method to social media as Mr. Lee, his major level about revealing one’s whereabouts and habits on a public on-line platform like Twitter is price retaining in thoughts.
Posting a photograph of you in entrance of the home you’ve just lately moved into, then later complaining that your landlord nonetheless hasn’t mounted that downstairs window, after which saying to the world that you just’re about to go on vacation for a few weeks, might all add as much as you coming again house to a nasty shock.
9. Decide out of sharing knowledge
Lastly, learn the phrases and circumstances of the stuff you join, and choose out of knowledge sharing the place you possibly can. It’s tempting to click on or faucet by the welcome or set up screens with out paying any consideration to what they’re saying. Very often you might have the chance to restrict the info you share with that firm, however it’s essential learn these screens to know if it’s essential tick a field or click on the Decline button.
Additionally, reasonable what you share on-line, and be savvy about how somebody your profile would possibly be a part of the dots. Use some type of multi-factor authentication, however don’t have codes despatched to you by way of SMS if in any respect attainable, and think about using a password supervisor and a VPN to higher shield your self and your on-line exercise.


