Be a part of prime executives in San Francisco on July 11-12, to listen to how leaders are integrating and optimizing AI investments for achievement. Study Extra
Final week, a U.S. federal authorities worker and Air Nationwide Guardsman named Jack Texeira was alleged to have exploited his Prime Secret clearance and leaked dozens of inner Pentagon paperwork to a Discord server, together with delicate info associated to the Russia-Ukraine battle.
The breach is a basic instance of a malicious insider assault, the place a privileged consumer decides to exfiltrate invaluable info. It additionally highlights that organizations have to act beneath the idea that any worker or contractor can determine to leak knowledge property at any time.
In reality, analysis reveals that insider threats are extremely widespread. Cyberhaven discovered that almost one in 10 workers (9.4%) will exfiltrate knowledge over a six-month interval, with buyer knowledge (44.6% of incidents) and supply code (13.8%) being the commonest property leaked.
“Privileged customers typically preserve an overabundance of standing entry to important programs and delicate knowledge, which, if extreme or pointless, can expose organizations to knowledge leaks,” stated Geoff Cairns, Forrester principal analyst. For that reason, “id administration is important to stopping id sprawl and imposing the precept of least privilege.”
Occasion
Rework 2023
Be a part of us in San Francisco on July 11-12, the place prime executives will share how they’ve built-in and optimized AI investments for achievement and prevented widespread pitfalls.
Register Now
Nonetheless, for Accel-backed knowledge safety startup Veza, safety groups have to go nicely past id administration to mitigate the dangers brought on by malicious insiders; they want granular visibility into human and machine identities all through the enterprise and what knowledge these identities have entry to.
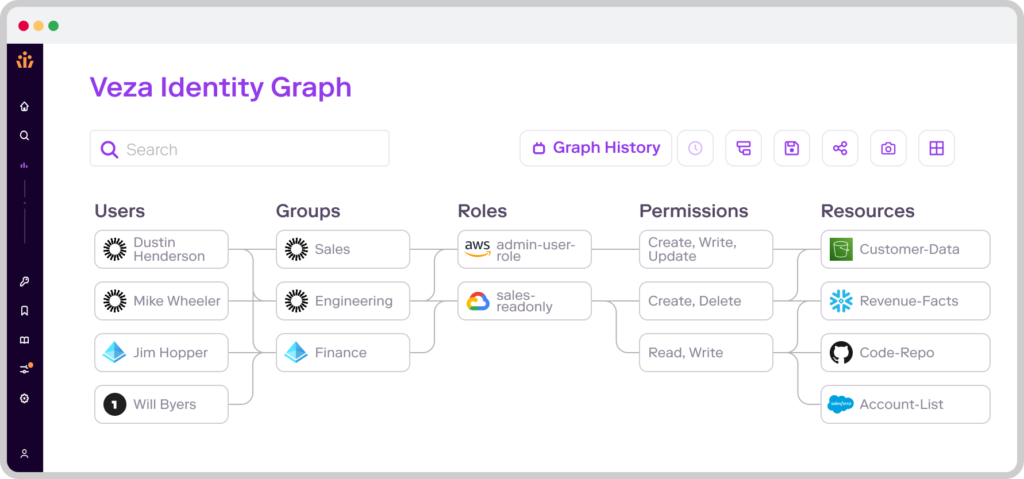
Unveiling the identity-to-data relationship

Conventional id administration is about establishing a course of for authenticating customers earlier than they will entry property. Whereas this strategy is important to enterprise safety, it’s not all the time clear what knowledge a person has entry to, notably when the common consumer has over 30 digital identities.
“We name it the id iceberg,” stated Tarun Thakur, CEO of Veza, in an unique interview with VentureBeat. “This commentary that now we have had since we based the corporate is admittedly the issue assertion of who has entry to what and what can they do? Organizations don’t have a solution to that query.”
With fashionable enterprises sustaining a median of 254 purposes, it’s tough to attain granular visibility into the precise knowledge property a given id or account can entry.
“Utilizing Nike for example,” Thakur started, “we are able to see [for example a user named] Gillian belongs to Nike, and our username Gillian or Gillian@nike.com. However what can Gillian do? What can she learn? What can she delete? What can she replace?”
Veza’s reply to the problem of knowledge visibility was to create an AI/ML mannequin engine to ingest role-based entry management (RBAC) metadata from a whole bunch of apps to construct an id menace graph.
The graph highlights the identity-to-data relationship, displaying human customers every id, what property they will entry and what actions they will carry out (e.g. whether or not they have learn or write permissions). As soon as this info is found, safety groups can management authorization and app permissions from a single location and scale back their organizations’ publicity to malicious insiders.
This strategy is totally different from conventional id administration instruments like Sailpoint and Okta as a result of it’s primarily based on highlighting the connection between identities and knowledge entry and defining controls, somewhat than hardening the id perimeter in opposition to menace actors with single sign-on (SSO) or adaptive, risk-based authentication.
The function of privileged entry administration
Mapping human and machine identities is only one step on the highway towards imposing zero-trust entry on the knowledge degree, as organizations additionally have to implement entry controls to attenuate the chance of knowledge leakage. This begins by implementing what Michael Kelley, senior director analyst at Gartner, calls “the precept of least privilege.”
The precept of least privilege implies that “solely the suitable individual has the suitable degree of entry, for the suitable cause, to the suitable useful resource, on the proper time,” Kelley stated. Every worker solely has entry to the recordsdata and assets essential to carry out their operate, nothing extra.
Each Veza and identity-data mapping present organizations with the flexibility to focus on privileges on the knowledge degree so there’s no ambiguity or threat of granting customers over-privileged entry.
That being stated, Kelley argues that organizations who wish to mitigate account takeover have to transcend implementing the precept of least privilege, arguing that “firms should then mitigate the chance of privileged accounts by PAM [privileged access management] practices,” Kelley stated.
In observe, which means discovering accounts with privilege, figuring out individuals or machines with entry to the accounts, after which discovering the extent of entry held by that account.
As soon as these high-value privileged accounts are recognized, they are often locked inside a single vault with a PAM answer. This allows approved customers to log in to the account to entry knowledge property, whereas the safety workforce audits and screens their exercise to verify no dangerous exercise, reminiscent of knowledge exfiltration, takes place.
The choice whether or not to include id administration, PAM, or identity-data mapping ought to be primarily based on a company’s particular wants.
For cloud-native organizations or these working in a hybrid cloud setting, automated mapping is important for getting visibility over human and machine identities that exist in a decentralized setting, as is implementing authorization controls on the knowledge degree.