Be a part of high executives in San Francisco on July 11-12, to listen to how leaders are integrating and optimizing AI investments for fulfillment. Be taught Extra
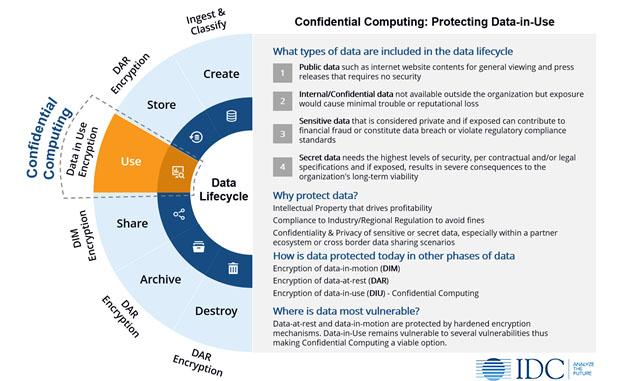
For enterprises to understand the potential that real-time datasets can ship, cloud tech stacks want hardening with zero belief. On this, confidential computing is important to securing knowledge at relaxation, in transit and in use.
VentureBeat spoke with CIOs from banking, monetary providers and insurance coverage industries who say they’re at numerous levels of piloting confidential computing to see how properly it handles their compliance, regulatory reporting and real-time auditing of knowledge transactions. Notably, compliance and help for zero belief frameworks are rising because the killer apps.
One CIO who spoke on situation of anonymity stated that their board of administrators’ staff assigned to danger administration needs to see proof that knowledge is secured throughout use inside protected CPU enclaves and Trusted Execution Environments (TEEs), two foundational parts of confidential computing.
Board members on danger administration groups recall Meltdown and Spectre vulnerabilities that focus on processors that depend on department prediction and superior speculative actions. CIOs and CISOs say boards have to see pilot knowledge and simulated assaults thwarted earlier than they go into manufacturing with confidential computing.
Occasion
Rework 2023
Be a part of us in San Francisco on July 11-12, the place high executives will share how they’ve built-in and optimized AI investments for fulfillment and averted frequent pitfalls.
Register Now
Primarily based on interval pilots that VentureBeat is briefed on, it’s clear that confidential computing strengthens zero belief in multicloud tech stacks on which extremely regulated companies depend on. Compliance, privateness, and safety use instances, notably on public cloud, have gained essentially the most important traction, accounting for 30 to 35% of the worldwide market, in keeping with Everest Teams’ report Confidential Computing: The Subsequent Frontier in Knowledge Safety. And, the confidential computing market is predicted to develop to $54 billion by 2026.

What’s confidential computing?
Confidential Computing is a cloud computing expertise that secures knowledge throughout processing by isolating delicate knowledge in a protected CPU enclave. The contents of every enclave, together with the information and evaluation methods, are solely accessed with approved programming codes, remaining invisible and shielded from exterior entry.
Confidential computing is gaining momentum as a result of it offers higher knowledge confidentiality, knowledge and code integrity than present safety applied sciences defending cloud tech stacks and infrastructure.
The Confidential Computing Consortium (CCC) is instrumental in selling and defining confidential computing throughout the business. The CCC is a Linux Basis challenge that mixes the efforts of {hardware} distributors, cloud suppliers and software program builders to assist enhance the adoption and standardization of TEE applied sciences.
TEEs defend proprietary enterprise logic, analytics capabilities, machine studying (ML) algorithms and purposes. Founding members embrace Alibaba, Arm, Google, Huawei, Intel, Microsoft and Purple Hat. The CCC defines confidential computing as defending knowledge in use by computing in a hardware-based TEE.

Compliance a development driver
What’s working in confidential computing’s favor with boards is how efficient it’s at making certain regulatory compliance. It’s additionally confirmed to be efficient at imposing end-to-end safety and least privileged entry to knowledge at relaxation, in transit and in use. CIOs and CISOs inform VentureBeat that they count on confidential computing to be complimentary to their Zero Belief Community Entry (ZTNA) frameworks and supporting initiatives.
John Kindervag created zero belief and presently serves as SVP for cybersecurity technique and is a gaggle fellow at ON2IT Cybersecurity. He’s additionally an advisory board member for a number of organizations, together with to the workplaces of the CEO and president of the Cloud Safety Alliance.
He lately informed VentureBeat that “the most important and best-unintended consequence of zero belief was how a lot it improves the power to cope with compliance and auditors.” And, he stated {that a} Forrester shopper known as and knowledgeable him how completely aligned zero belief was with their compliance and audit automation course of.
Securing cloud tech stacks with confidential computing
Mark Russinovich, CTO and technical fellow of Microsoft Azure writes that: “Our imaginative and prescient is to remodel the Azure cloud into the Azure confidential cloud, shifting from computing within the clear to computing confidentially throughout the cloud and edge. We wish to empower prospects to realize the very best ranges of privateness and safety for all their workloads.”
Cloud platform suppliers endorsed and commenced integrating CCC’s necessities into their product roadmaps as early as 2019, when the CC was fashioned. What’s guiding cloud platform suppliers is the purpose of offering their prospects with the technical controls essential to isolate knowledge from cloud platform operators, their operators, or each.
Microsoft’s Azure confidential computing is taken into account an business chief as a result of their DevOps groups designed the platform to transcend hypervisor isolation between buyer tenants to safeguard buyer knowledge from Microsoft operator entry.
CIOs and CISOs have recognized to VentureBeat what they’re in search of with regards to a baseline degree of efficiency with confidential computing. First, distant attestation must be confirmed in stay buyer websites with referenceable accounts keen to talk to how they’re utilizing it to test the integrity of the setting. Second, trusted launch workflows and processes ideally have to be cloud-based, in manufacturing, and confirmed to validate digital machines beginning up with approved software program and steady distant attestation to test for purchasers.
Silicon-based zero belief is the way in which
Martin G. Dixon, Intel fellow and VP of Intel’s safety structure and engineering group writes that, “I imagine the zero belief ideas shouldn’t cease on the community or system. Reasonably, they are often utilized down contained in the silicon. We even seek advice from infrastructure on the chip as a community or ‘community on a chip.’”
A part of that imaginative and prescient at Intel included the necessity for attestation to change into extra pervasive and moveable to gas confidential computing’s development, beginning on the silicon degree.
To deal with this, the corporate launched Mission Amber, whose objectives embrace offering impartial attestation, extra uniform, moveable attestation and improved coverage verification.
“With the introduction of Mission Amber, Intel is taking confidential computing to the following degree in our dedication to a zero belief strategy to attestation and the verification of compute property on the community, edge and within the cloud,” Greg Lavender, Intel’s CTO stated on the firm’s Intel Imaginative and prescient convention final 12 months.
He continued that Intel is targeted on “extending attestation providers within the cloud knowledge heart within the edge computing environments to offer unprecedented safety. The Intel Software program as a Service providing Mission Amber is a trusted service resolution that can present organizations with impartial verification and trustworthiness of buyer property regardless of the place they run.”

Getting silicon-based zero belief safety proper wants to begin with TEEs hardened sufficient to guard delicate knowledge at relaxation, in transit and in use. Migrating zero belief into silicon additionally strengthens authentication and authorization, taking identification and entry administration (IAM) and privileged entry administration to the {hardware} degree, which makes it tougher for attackers to bypass or manipulate authentication methods and improves the safety of confidential computing environments.
Further advantages of shifting zero belief into silicon embrace encrypting all knowledge and making certain a better degree of knowledge integrity and making use of zero belief ideas to knowledge encryption and authentication. With zero belief frameworks requiring steady safety configuration and posture validation for all customers and gadgets, supporting monitoring in silicon will cut back the overhead on cloud platform efficiency.