Be part of prime executives in San Francisco on July 11-12, to listen to how leaders are integrating and optimizing AI investments for fulfillment. Study Extra
One of many major causes corporations maintain being breached is that they don’t know what number of endpoints are on their networks and what situation these endpoints are in. CISOs inform VentureBeat that unifying endpoint safety and identities will assist to scale back the variety of unknown endpoints and harden id administration towards future assaults. However most organizations are nonetheless flying blind when it comes to understanding the present state of each community endpoint.
Cybercriminal gangs, superior persistent risk (APT) teams and different cyberattackers know that almost all organizations have an imprecise depend of their endpoints. These teams are additionally very conscious of the huge hole between endpoint safety and id safety. They use ChatGPT and different generative AI instruments to fine-tune their tradecraft and launch assaults.
Sixty p.c of enterprises are conscious of lower than 75% of the endpoint gadgets on their community. Solely 58% can determine each attacked or susceptible asset on their community inside 24 hours of an assault or exploit. It’s a digital pandemic nobody needs to speak about as a result of everybody is aware of a company and staff that’s been burned by not understanding about each endpoint. It’s additionally frequent to seek out organizations which might be failing to trace as much as 40% of their endpoints.
Endpoints must ship better resilience to show their worth
CISOs and CIOs inform VentureBeat that with income falling wanting forecasts, cybersecurity budgets have come underneath elevated scrutiny. New gross sales cycles are taking longer, current prospects are asking for worth breaks and prolonged phrases, and it’s proving to be a difficult yr for locating new enterprise prospects, in line with CISOs VentureBeat interviewed throughout the monetary companies, insurance coverage and manufacturing sectors.
Occasion
Remodel 2023
Be part of us in San Francisco on July 11-12, the place prime executives will share how they’ve built-in and optimized AI investments for fulfillment and averted frequent pitfalls.
Register Now
“To maximise ROI within the face of finances cuts, CISOs might want to exhibit funding into proactive instruments and capabilities that constantly enhance their cyber-resilience,” mentioned Marcus Fowler, CEO of AI cybersecurity firm Darktrace.
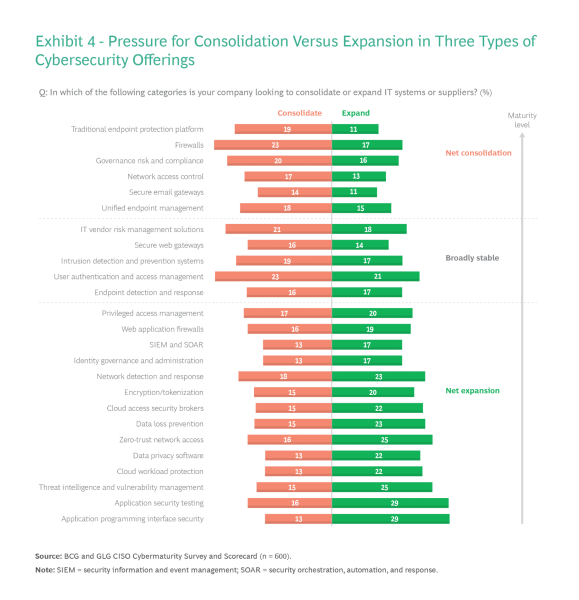
Boston Consulting Group (BCG) wrote in its current article As Budgets Get Tighter, Cybersecurity Should Get Smarter that “CISOs will probably be pressed to discover elevated coaching, course of enhancements, and shifts in company tradition to enhance their safety postures with out increasing their budgets.”

BCG additionally reported that 78% of superior corporations usually measure the ROI of their cyber-operation enhancements. Consolidation is a excessive precedence, as VentureBeat has found within the many interviews it has with CISOs. The BCG research discovered that firewalls, consumer authentication and entry administration, and endpoint safety platforms are among the many commonest areas the place CISOs search to consolidate spending. In brief, for endpoint safety platforms to maintain their place in budgets, they have to ship better resilience.
“After we’re speaking to organizations, what we hear a whole lot of is: How can we proceed to extend resiliency, improve the way in which we’re defending ourselves, even within the face of probably both decrease headcount or tight budgets? And so it makes what we do round cyber-resiliency much more essential,” mentioned Christy Wyatt, president and CEO of Absolute Software program, in a BNN Bloomberg interview. “One of many distinctive issues we do is assist individuals reinstall or restore their cybersecurity property or different cybersecurity purposes. So a quote from one in every of my prospects was: It’s like having one other IT individual within the constructing.”
The High 10 endpoint safety challenges — and potential options
Enhancing any group’s endpoint safety posture administration calls for a give attention to consolidation. Because the BCG research illustrates, CISOs are underneath vital strain to consolidate their endpoint safety platforms. Search for the main suppliers of endpoint safety platforms (EPPs), endpoint detection and response (EDR) and prolonged detection and response (XDR) to both purchase extra complementary applied sciences or fast-track improvement internally to drive extra consolidation-driven gross sales. Amongst these suppliers are Absolute Software program, BitDefender, CrowdStrike, Cisco, ESET, FireEye, Fortinet, F-Safe, Ivanti, Microsoft, McAfee, Palo Alto Networks, Sophos and Zscaler.
The highest 10 challenges that may outline their M&A, DevOps and expertise partnership methods are the next:
1. Not having sufficient real-time telemetry information to increase endpoint lifecycles and determine intrusions and breaches
Actual-time telemetry information from endpoints is desk stakes for a profitable endpoint safety technique that may to determine an intrusion or breach in progress. It’s additionally invaluable for figuring out the {hardware} and software program configuration of each endpoint, to each stage — file, course of, registry, community connection and system information.
Absolute Software program, BitDefender, CrowdStrike, Cisco, Ivanti, and Microsoft Defender for Endpoint, which secures endpoint information in Microsoft Azure, in addition to different main distributors seize real-time telemetry information and use it to derive endpoint analytics.
CrowdStrike, ThreatConnect, Deep Intuition and Orca Safety use real-time telemetry information to calculate indicators of assault (IOAs) and indicators of compromise (IOCs). IOAs give attention to detecting an attacker’s intent and figuring out their objectives, whatever the malware or exploit utilized in an assault. Complementing IOAs are indicators of compromise (IOC) that present forensics to show a community breach.
IOAs have to be automated to supply correct, real-time information to be able to perceive attackers’ intent and cease intrusion makes an attempt. CrowdStrike was the primary to launch AI-powered IOAs that capitalize on real-time telemetry information to guard endpoints. The corporate says AI-powered IOAs work asynchronously with sensor-based machine studying and different sensor protection layers.
2. Overconfigured, overloaded endpoints — a breach ready to occur
CISOs inform VentureBeat it’s frequent for endpoints to have a number of, generally over a dozen, endpoint brokers put in. Usually as one CISO leaves and one other is employed, one in every of their first actions is putting in their most well-liked endpoint system. Reminiscence conflicts, faults and efficiency drains are frequent. Absolute’s 2023 Resilience Index discovered that the everyday enterprise’s endpoint gadgets have over 11 safety apps put in, with a mean of two.5 apps for endpoint administration alone, adopted by antivirus/anti-malware (2.1 apps on common) and encryption (1.6 apps). CISOs inform VentureBeat that overloading endpoints is a typical drawback, usually introduced on when new safety groups and managers are coming in.
What makes this one of the vital difficult issues to resolve is that endpoints are so overbuilt with prerequisite software program for every consumer. CISOs advocate totally auditing the grasp photos for every endpoint kind or class after which consolidating them all the way down to the naked minimal of brokers. This helps scale back prices and improves efficacy, visibility and management.
3. Counting on legacy patch administration programs that pressure system inventories
CISOs say their groups are already stretched skinny maintaining networks, programs and digital workers safe. They usually run out of time earlier than patches should be put in. Seventy-one p.c of IT and safety professionals discover patching too sophisticated and time-consuming, and 53% spend most of their time organizing and prioritizing essential vulnerabilities.
VentureBeat has discovered via earlier CISO and CIO interviews that taking a data-driven strategy can assist. One other innovation that a number of distributors are utilizing to sort out this drawback is synthetic intelligence (AI) and machine studying (ML).
Ivanti’s State of Safety Preparedness 2023 Report discovered that 61% of the time, an exterior occasion, intrusion try or breach reinitiates patch administration efforts. Although organizations are racing to defend towards cyberattacks, the trade nonetheless has a reactive, guidelines mentality.
“With greater than 160,000 vulnerabilities presently recognized, it’s no surprise that IT and safety professionals overwhelmingly discover patching overly advanced and time-consuming,” Dr. Srinivas Mukkamala, chief product officer at Ivanti, informed VentureBeat throughout a current interview. “Because of this organizations should make the most of AI options … to help groups in prioritizing, validating and making use of patches. The way forward for safety is offloading mundane and repetitive duties suited to a machine to AI copilots in order that IT and safety groups can give attention to strategic initiatives for the enterprise.”
Leaders on this space embrace Automox, Ivanti Neurons for Patch Intelligence, Kaseya, ManageEngine and Tanium.
4. Holding BYOD asset configurations present and in compliance
Holding corporate-owned system configurations present and compliant takes nearly all of time safety groups can dedicate to endpoint asset administration. Groups usually don’t get to BYOD endpoints, and IT departments’ insurance policies on workers’ personal gadgets are generally too broad to be beneficial. Endpoint safety platforms must streamline and automate workflows for configuring and deploying company and BYOD endpoint gadgets.
Main endpoint platforms that may do that immediately at scale and have delivered their options to enterprises embrace CrowdStrike Falcon, Ivanti Neurons and Microsoft Defender for Endpoint, which correlates risk information from emails, endpoints, identities and purposes.
5. Implementing a focused UEM technique to dam assaults geared toward senior administration over their cellular gadgets
Whale phishing is the newest type of cyberattack, affecting hundreds of C-suites. Ivanti’s State of Safety Preparedness 2023 Report discovered that executives are 4 instances extra more likely to grow to be phishing victims than workers are. Practically one in three CEOs and members of senior administration have fallen sufferer to phishing scams, both by clicking on a hyperlink or sending cash.
Adopting a unified endpoint administration (UEM) platform is important for shielding each cellular system. Superior UEM platforms can automate configuration administration and guarantee company compliance to scale back breach threat.
CISOs need UEM platform suppliers to consolidate and provide extra worth at decrease value. Gartner’s newest Magic Quadrant for Unified Endpoint Administration Instruments displays CISOs’ impression on the product methods at IBM, Ivanti, ManageEngine, Matrix42, Microsoft, VMWare, Blackberry, Citrix and others.
6. Too many IT, safety and contractor staff members with admin entry to endpoints, purposes and programs
Beginning on the supply, CISOs must audit entry privileges and determine former workers, contractors and distributors who nonetheless have admin privileges outlined in Lively Listing, id and entry administration (IAM) and privileged entry administration (PAM) programs. All identity-related exercise ought to be audited and tracked to shut belief gaps and scale back the specter of insider assaults. Pointless entry privileges, similar to these of expired accounts, have to be eradicated.
Kapil Raina, vp of zero-trust advertising at CrowdStrike, informed VentureBeat that it’s a good suggestion to “audit and determine all credentials (human and machine) to determine assault paths, similar to from shadow admin privileges, and both mechanically or manually modify privileges.”
7. The numerous identities that outline an endpoint want simpler key and digital certificates administration
Each machine in a community requires a novel id so directors can handle and safe machine-to-machine connections and communications. However endpoints are more and more taking up extra identities, making it a problem to safe every id and the endpoint concurrently.
That’s why extra focus is required on key and digital certificates administration. Digital identities are assigned by way of SSL, SSH keys, code-signing certificates, TLS or authentication tokens. Cyberattackers goal SSH keys, bypassing code-signed certificates or compromising SSL and TLS certificates.
Safety groups’ goal is to make sure each id’s accuracy, integrity and reliability. Main suppliers on this space embrace CheckPoint, Delinea, Fortinet, IBM Safety, Ivanti, Keyfactor, Microsoft Safety, Venafi and Zscaler.
8. Unreliable endpoint programs that break simply, ship too many false positives and take hours to repair
CISOs inform VentureBeat that that is probably the most difficult drawback to resolve — endpoints that may’t reset themselves after a reconfiguration or, worse, require guide workarounds that take an inordinate quantity of assets to handle.
Changing legacy endpoint programs with self-healing endpoints helps scale back software program agent sprawl. By definition, a self-healing endpoint will shut itself down and validate its core parts, beginning with its OS. Subsequent, the endpoint will carry out patch versioning, then reset itself to an optimized configuration with out human intervention.
Absolute Software program gives an undeletable digital tether to each PC-based endpoint to observe and validate real-time information requests and transactions. Akamai, Ivanti, Malwarebytes, Microsoft, SentinelOne, Tanium and Development Micro are main suppliers of self-healing endpoints. Absolute’s Resilience platform is noteworthy for offering real-time visibility and management of any system, whether or not it’s on the community or not.
9. Counting on a set of standalone instruments to shut endpoint gaps or get a 360-degree view of threats
Normalizing stories throughout standalone instruments is tough, time-consuming and costly. It requires SOC groups to manually correlate threats throughout endpoints and identities. Seeing all exercise on one display isn’t potential as a result of instruments use completely different alerts, information constructions, reporting codecs and variables.
Mukkamala’s imaginative and prescient of managing each consumer profile and consumer system from a single pane of glass is shared by the CISOs VentureBeat interviewed for this text.
10. Closing the gaps in identity-based endpoint safety with multifactor authentication (MFA) and passwordless applied sciences
To get MFA buy-in from workers throughout the corporate, CISOs and safety groups ought to begin by designing it into workflows and minimizing its impression on consumer experiences. Groups additionally want to remain present on passwordless applied sciences, which is able to finally alleviate the necessity for MFA, delivering a streamlined consumer expertise.
Main passwordless authentication suppliers embrace Microsoft Azure Lively Listing (Azure AD), OneLogin Workforce Identification, Thales SafeNet Trusted Entry and Home windows Hey for Enterprise.
Implementing id administration on cellular gadgets has grow to be a core requirement as extra workforces keep digital. Of the options on this space, Ivanti’s Zero Signal-On (ZSO) is the one one that mixes passwordless authentication, zero belief and a streamlined consumer expertise on its unified endpoint administration (UEM) platform.
Ivanti’s answer is designed to help biometrics (Apple’s Face ID) because the secondary authentication issue for accessing private and shared company accounts, information and programs. Ivanti ZSO eliminates the necessity for passwords by utilizing FIDO2 authentication protocols. It may be configured on any cellular system and doesn’t want one other agent to remain present, CISOs inform VentureBeat.
With AI-driven breaches, the long run is now
Attackers are sharpening their tradecraft to use unprotected endpoints, capitalize on gaps between endpoints and unprotected identities and go whale phishing greater than ever earlier than. Safety and IT groups should tackle the challenges of bettering endpoint safety in response. AI and machine studying are revolutionizing endpoint safety, and the ten challenges briefly mentioned on this article are driving new product improvement throughout many cybersecurity startups and main distributors.
Each group must take these steps to guard itself from attackers who’re already utilizing generative AI, ChatGPT and superior, multifaceted assaults to steal identities and privileged entry credentials and breach endpoints undetected.