Take a look at the on-demand periods from the Low-Code/No-Code Summit to discover ways to efficiently innovate and obtain effectivity by upskilling and scaling citizen builders. Watch now.
As data-driven enterprises rely closely on their software program utility structure, utility programming interfaces (APIs) occupy a big place. APIs have revolutionized the way in which net functions are used, as they help communication pipelines between a number of companies. Builders can combine any trendy expertise with their structure by utilizing APIs, which is very helpful for including options {that a} buyer wants.
By nature, APIs are susceptible to exposing utility logic and delicate information reminiscent of personally identifiable info (PII), which makes them a simple goal for attackers. Usually accessible over public networks (accessible from wherever), APIs are sometimes well-documented and might be rapidly reverse-engineered by malicious actors. They’re additionally inclined to denial of service (DDoS) incidents.
Probably the most vital information leaks are on account of defective, susceptible or hacked APIs, which may reveal medical, monetary and private information to most of the people. As well as, numerous assaults can happen if an API just isn’t secured appropriately, making API safety a significant facet for data-driven companies immediately.
Why API safety is crucial
API improvement has astronomically elevated over the previous few years, fueled by digital transformation and its central function in cellular apps and IoT improvement. Such development and a wide range of attainable assaults make API safety extremely important.
Occasion
Clever Safety Summit
Be taught the essential function of AI & ML in cybersecurity and business particular case research on December 8. Register to your free cross immediately.
Register Now
As microservices and serverless architectures have change into extra widespread, assaults embody bypassing the client-side utility to disrupt the functioning of an utility for different customers or to breach personal info. Moreover, damaged, uncovered or hacked APIs can even result in breaches of the backend system.
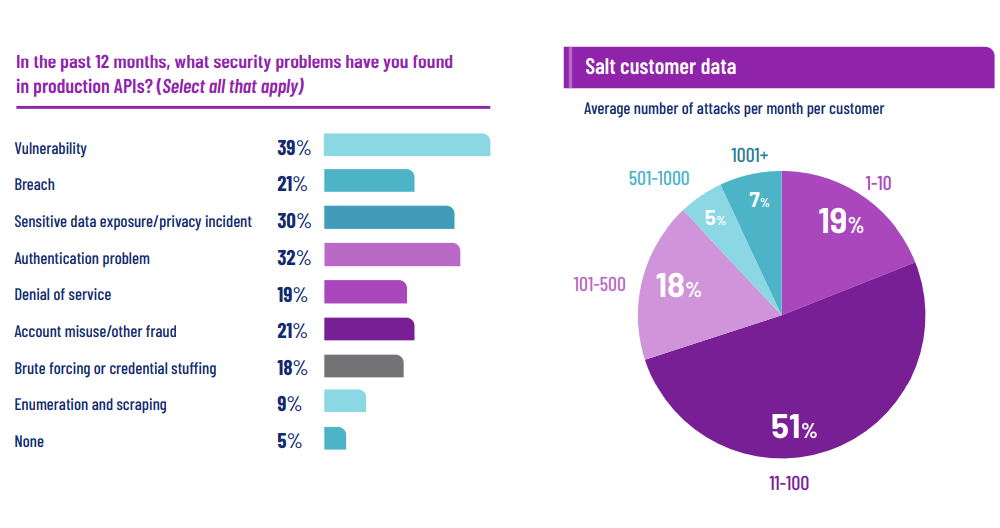
In its API Safety and Administration report [subscription required], Gartner predicts that by 2023, API abuses will transfer from rare to probably the most frequent assault vector, leading to information breaches for enterprise net functions, and by 2025, greater than 50% of information theft shall be on account of unsecure APIs.
“At Gartner, we repeatedly converse with organizations which have suffered breaches of their APIs,” Mark O’Neill, VP analyst at Gartner, informed VentureBeat. “APIs are significantly susceptible as a result of many safety groups are much less expert in API safety. That is significantly regarding for newer API sorts reminiscent of GraphQL.”
Given the essential function they play in digital transformation and the entry to delicate information and techniques they supply, APIs now demand a devoted strategy to safety and compliance.
API safety vs. utility safety
API safety focuses on securing this utility layer and addressing what can occur if a malicious hacker interacts with the API immediately. API safety additionally includes implementing methods and procedures to mitigate vulnerabilities and safety threats.
When delicate information is transferred by API, a protected API can assure the message’s secrecy by making it accessible to apps, customers and servers with applicable permissions. It additionally ensures content material integrity by verifying that the data was not altered after supply.
“Any group wanting ahead to digital transformation should leverage APIs to decentralize functions and concurrently present built-in companies. Subsequently, API safety must be one of many key focus areas,” mentioned Muralidharan Palanisamy, chief options officer at AppViewX.
Speaking about how API safety differs from basic utility safety, Palanisamy mentioned that utility safety is much like securing the primary door, which wants strong controls to stop intruders. On the identical time, API safety is all about securing home windows and the yard.
“A weak level in such areas will have an effect on the applying. API safety, in essence, is a subset of the entire utility safety with out which the applying as a complete can’t be secured,” he mentioned.
Erez Yalon, VP of safety analysis at Checkmarx, says that API safety just isn’t totally different from conventional appsec, however it provides extra areas that organizations want to concentrate to.
“API-centric structure has extra endpoints {that a} potential attacker can attempt to abuse; we name this ‘development of assault floor,’” he mentioned. “As well as, the way in which that information is transferred and shared by APIs makes it simple to unintentionally expose delicate information to prying eyes.”
Yalon mentioned that APIs could possibly be made safer when safety is taken into account from step one and the primary line of code written, as a substitute of added as an extra layer later within the recreation.
“Each API endpoint must be documented, and organizations should have clear pointers on deprecating outdated and unused APIs. Ensuring an up to date SBOM [software bill of materials] exists makes it easier,” mentioned Yalon.
Important API vulnerabilities and assaults
APIs have rapidly established themselves as the popular methodology of constructing trendy functions, particularly for cellular gadgets and the web of issues (IoT). Nonetheless, within the face of continually altering application-development strategies and pressures for innovation, some corporations nonetheless want to completely grasp the potential dangers related to making their APIs accessible to the general public. Earlier than public deployment, companies should be cautious of those frequent safety errors:
- Authentication flaws: Many APIs reject authentication standing requests from a real consumer. An attacker can replicate API requests by exploiting such deficiencies in numerous methods, together with session hijacking and account aggregation.
- Lack of encryption: Many APIs lack strong encryption layers between the API shopper and server. Attributable to such flaws, attackers can intercept unencrypted or poorly protected API transactions, steal delicate information or alter the transaction information.
- Flawed endpoint safety: As most IoT gadgets and microservice instruments are designed to speak with the server by an API channel, hackers try to achieve management over them by IoT endpoints. Doing so can typically resequence the API order, leading to an information breach.
Present challenges in API safety
In keeping with Yannick Bedard, head of penetration testing, IBM safety X-Pressure Crimson, one of many present challenges in API safety is them being examined for security, as meant logic flows could also be difficult to know and check for if not clearly outlined.
“In an internet utility, these logical flows are intuitive by using the net UI, however in an API, it may be harder to element these workflows,” Bedard informed VentureBeat. “This may result in safety testing lacking vulnerabilities that will, in flip, be exploited by attackers.”
Bedard mentioned that as pipelining of APIs turns into increasingly complicated, there typically arises questions of which service is accountable for what facet of safety and at what level the information is taken into account “clear.”
“It’s common for companies to inherently belief information coming from different APIs as clear, just for it to prove to not be correctly sanitized,” he mentioned.
Bernard says that an instance of this was the preliminary discovery of the Log4J vulnerability, the place most corporations targeted totally on what that they had immediately internet-facing.
“Malicious information would finally movement to backend APIs, typically behind many different companies. These APIs would, in flip, be susceptible and will present the attacker an preliminary foothold into the group,” he mentioned.
“The highest problem is discovery, as many safety groups simply aren’t certain what number of APIs they’ve,” mentioned Sandy Carielli, principal analyst at Forrester.
Carielli mentioned that many groups unknowingly deploy rogue APIs or there could also be unmaintained APIs which might be nonetheless publicly accessible, which may result in a number of safety hazards.
“API specs could possibly be outdated, and you’ll’t shield what you don’t know you could have,” she mentioned. “Begin by understanding what controls you have already got in your atmosphere to safe APIs, after which determine and handle the gaps. Critically, be certain to handle API discovery and stock.”
Finest practices to boost API safety
The energy of API safety relies upon totally upon how one’s information structure enforces authentication and authorization insurance policies. Due to technological advances like cloud companies, API gateways and integration platforms now enable API suppliers to safe their APIs in distinctive methods. The expertise stack on which you select to construct your APIs impacts the way you safe them.
A number of approaches could also be used to successfully defend your system in opposition to API intruders:
- API gateway: An API gateway is the muse of an API safety framework because it makes it easy to develop, preserve, monitor and safe APIs. The API gateway can defend in opposition to numerous threats and supply API monitoring, logging and fee limitation. It could actually additionally automate safety token validation and visitors restriction based mostly on IP addresses and different information.
- Net utility firewalls: An online utility firewall or WAF, acts as a center layer between public visitors and the API gateway or utility. WAFs can provide extra safety in opposition to risk actors, reminiscent of bots, by offering malicious bot detection, the power to determine assault signatures, and extra IP intelligence. WAFs might be useful for blocking dangerous visitors earlier than it even reaches your gateway.
- Safety functions: Standalone safety merchandise that assist options reminiscent of real-time safety, static code and vulnerability scanning, built-time checking, and safety fuzzing can be inculcated throughout the safety structure.
- Safety in code: Safety code is a type of safety carried out internally into the API or functions. Nonetheless, the sources required to make sure all the safety measures are carried out appropriately in your API code might be troublesome to use constantly throughout all of your API portfolios.
The way forward for API safety
Roy Liebermann, head of buyer success at Surf Safety, believes that zero belief might be one other different to defend in opposition to inside and exterior threats.
“In relation to APIs, zero belief is related for each purchasers and servers,” he mentioned. “An API-driven utility can have an unlimited variety of microservices, making it troublesome for safety leaders to trace their improvement and safety affect. Adopting zero-trust ideas ensures that every microservice communicates with the least privilege, stopping using open ports and enabling authentication and authorization throughout every API.”
Liebermann recommends that CISOs prolong zero belief to APIs to cut back the chance of hackers exploiting API communication to steal information.
Likewise, Palanisamy says that as zero-trust safety and zero-trust architectures acquire momentum, API safety shall be one of many fundamental focus areas, particularly with SaaS and different cloud companies used immediately.
“The hot button is to take a look at this with an enterprise-wide strategy. API safety can’t be solved by simply specializing in a number of functions,” he mentioned.
“We’re almost certainly going to see a distinct software program paradigm shift within the subsequent 5 years that mixes options from REST and SOAP safety. I imagine there shall be a software program improvement paradigm the place options from every methodology are used to create a mixed superior methodology,” Nabil Hannan, managing director at NetSPI, informed VentureBeat. “This mixture will take safety out of the fingers of the builders and permit for higher ‘safe by design’ adoption.”
Hannan mentioned that the idea of identification and authentication is altering, and we have to transfer away from usernames and passwords and two-factor authentication, which depends on people not making any errors.
“The authentication workflow will shift to what corporations like Apple are doing round identification administration with improvements just like the iOS16 keychain. This shall be developed by APIs within the close to future,” he mentioned.