Be part of high executives in San Francisco on July 11-12 and learn the way enterprise leaders are getting forward of the generative AI revolution. Be taught Extra
Healthcare suppliers should look past the cloud and undertake zero-trust safety to achieve preventing again towards the onslaught of breaches their trade is experiencing.
Attackers usually prey on gaps in community servers, incorrectly configured cloud configurations, unprotected endpoints, and weak to non-existent id administration and privileged entry safety. Stealing medical data, identities and privileged entry credentials is a excessive precedence for healthcare cyberattackers. On common, it takes a healthcare supplier $10.1 million to get well from an assault. 1 / 4 of healthcare suppliers say a ransomware assault has pressured them to cease operations utterly.
Healthcare should construct on cloud safety with zero belief
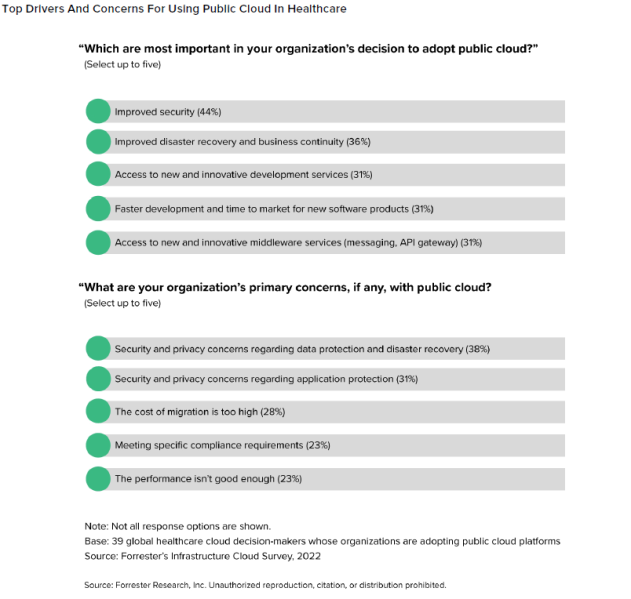
Forrester’s current report, The State of Cloud in Healthcare, 2023, gives an insightful have a look at how healthcare suppliers are fast-tracking their cloud adoption with the hope of getting cybersecurity underneath management. Eighty-eight p.c of world healthcare decision-makers have adopted public cloud platforms, and 59% are adopting Kubernetes to make sure larger availability for his or her core enterprise methods. On common, healthcare suppliers spend $9.5 million yearly throughout all public cloud platforms they’ve built-in into their tech stacks. It’s proving efficient — to a degree.
What’s wanted is for healthcare suppliers to double down on zero belief, first going all-in on id entry administration (IAM) and endpoint safety. Essentially the most insightful a part of the Forrester report is the proof it gives that persevering with developments from Amazon Net Companies, Google Cloud Platform, Microsoft Azure and IBM Cloud are hitting the mark with healthcare suppliers. Their mixed efforts to show cloud platforms are safer than legacy community servers are resonating.
Occasion
Remodel 2023
Be part of us in San Francisco on July 11-12, the place high executives will share how they’ve built-in and optimized AI investments for achievement and prevented frequent pitfalls.
Register Now
That’s good news for the trade, as the newest information from the U.S. Division of Well being and Human Companies (HHS) Breach Portal reveals that within the final 18 months alone, 458 healthcare suppliers have been breached by community servers, exposing over 69 million affected person identities.
The HHS portal reveals that this digital pandemic has compromised 39.9 million affected person identities within the first six months of 2023, harvested from 298 breaches. Of these, 229 resulted from profitable hacking, 61 from unauthorized entry/disclosure, and the rest from theft of medical data. Enterprise e-mail compromise (BEC) and pretexting are liable for 54 breaches since January, compromising 838,241 sufferers’ identities.
Thought of best-sellers on the Darkish Net, affected person medical data present a wealth of knowledge for attackers. Cybercrime gangs and globally organized superior persistent menace (APT) teams steal, promote and use affected person identities to create artificial fraudulent identities. Attackers are getting as much as $1,000 per file relying on how detailed the id and medical information are.
Classes from the 2023 Telesign Belief Index, which confirmed the rising fragility of digital belief, should even be utilized to healthcare.

Turning weaknesses into strengths with zero belief
Forrester concludes that healthcare suppliers are prime targets for attackers as a result of they use outdated legacy applied sciences, particularly when storing delicate affected person information. That weak point is magnified by the urgency of getting crucial care to sufferers.
“Menace actors are more and more focusing on flaws in cyber-hygiene, together with legacy vulnerability administration processes,” Srinivas Mukkamala, chief product officer at Ivanti, advised VentureBeat.
In actual fact, Ivanti’s Press Reset: A 2023 Cybersecurity Standing Report discovered that each one organizations are behind in defending towards ransomware, software program vulnerabilities, API-related assaults and software program provide chain assaults. Ivanti’s analysis outcomes underscore why zero belief must turn out to be an pressing precedence in all healthcare organizations, on condition that many lag behind friends in different industries on these core dimensions.
Forrester noticed that “CISOs could also be reluctant to belief the general public cloud, however outsourcing to a multitenant platform can profit healthcare suppliers with military-grade AES 256 information encryption that helps forestall information publicity and theft. World hyperscalers supply compliant cases and consulting companies to assist meet regulatory compliance. Equally, EHR methods akin to Oracle Cerner and Epic Methods are actually providing cloud-based choices/partnerships.”
Each healthcare supplier wants a zero-trust roadmap tailor-made to its best threats
The aim is to turn out to be extra resilient over time with out breaking budgets or asking for main investments from the board. A superb place to start out is with a zero-trust roadmap. There are a number of normal paperwork CISOs and CIOs operating healthcare IT and cybersecurity ought to use to tailor zero-trust safety to their distinctive enterprise challenges.
The primary is from the Nationwide Institute of Requirements and Expertise’s (NIST) Nationwide Cybersecurity Middle of Excellence (NCCoE). The NIST Cybersecurity White Paper (CSWP), Planning for a Zero Belief Structure: A Information for Federal Directors, describes processes for migrating to a zero-trust structure utilizing the NIST Danger Administration Framework (RMF).
Second, John Kindervag, who created zero belief whereas at Forrester and presently serves as senior vice chairman, cybersecurity technique and ON2IT group fellow at ON2IT Cybersecurity, and Dr. Chase Cunningham have been amongst a number of trade leaders who wrote the helpful President’s Nationwide Safety Telecommunications Advisory Committee (NSTAC) Draft on Zero Belief and Trusted Identification Administration. The doc defines zero-trust structure as “an structure that treats all customers as potential threats and prevents entry to information and assets till the customers could be correctly authenticated and their entry licensed.”
The Cybersecurity and Infrastructure Safety Company (CISA) publishes a hub of the President’s NSTAC Publications, offering a invaluable index of the committee’s physique of labor.
Proliferating ransomware assaults underscore the necessity to implement least privileged entry throughout each menace floor
“We all know that dangerous guys, as soon as they’re within the community and compromise [it], the primary [breached] machine can transfer laterally to the subsequent machine, after which the subsequent machine, and the subsequent machine. So as soon as they’ve figured that out, the possibilities of you having a ransomware breach and having information exfiltrated out of your setting improve,” Drex DeFord, govt strategist and healthcare CIO at CrowdStrike, advised VentureBeat throughout an interview.
The U.S. Division of Well being and Human Companies (HHS) Well being Sector Cybersecurity Coordination Middle (HC3) gives a collection of Menace Briefs that healthcare CISOs and CIOs ought to think about subscribing to and staying present with. The depth of study and perception the HCS places into these briefs is noteworthy.
To grasp the size of healthcare suppliers’ challenges with ransomware, VentureBeat additionally recommends studying the June 8, 2023 presentation, Kinds of Menace Actors That Threaten Healthcare.
One other temporary reveals how nation-state assaults are among the many most refined and difficult to cease: the November 3, 2022 Menace Transient titled “Iranian Menace Actors and Healthcare.”
Two excessive priorities, in accordance with CISOs: a compromise evaluation, and a subscription to an incident response retainer service
Healthcare suppliers and supporting organizations want a transparent baseline throughout all methods to confirm that their current IT environments and tech stacks are clear. “When you might have a compromise evaluation finished, [getting] a complete have a look at the whole setting and [making] positive that you simply’re not owned, and also you simply don’t understand it but, is extremely necessary,” DeFord advised VentureBeat throughout an interview.
DeFord and different CISOs interviewed for this text additionally advise healthcare CISOs to get an incident response retainer service in the event that they don’t have already got one. “That makes positive that ought to one thing occur, and also you do have a safety incident, you may name somebody, and they’ll come instantly,” DeFord advises.
IoT, edge computing and linked medical gadgets make endpoint safety a continuing battle
Most legacy IoT sensors, the machines connected to them, and medical gadgets aren’t designed with safety as a main aim. That’s why attackers love these gadgets. Dr. Srinivas Mukkamala, chief product officer at cybersecurity firm Ivanti, says enterprise leaders should understand the price of managing endpoints, IoT and medical gadgets by regularly enhancing safety. “Organizations should proceed transferring towards a zero-trust mannequin of endpoint administration to see round corners and bolster their safety posture,” Mukkamala advised VentureBeat.
Absolute Software program’s 2023 Resilience Index reveals that the common endpoint has 11 completely different safety brokers put in, every degrading at a distinct price and creating reminiscence conflicts. This leaves the endpoint unprotected and weak to a breach. Overloading endpoints with too many brokers is simply as dangerous as having none put in. CISOs and CIOs in healthcare must audit each endpoint agent put in and discover out if and the way they battle with one another.
A core a part of the audit is realizing which identities have entry rights for every endpoint, together with third-party contractors and suppliers. Captured audit information is invaluable in setting least privileged entry insurance policies that strengthen zero belief on each endpoint.
Defending affected person identities requires making zero belief a precedence
Healthcare CISOs are underneath strain to make sure their IT and cybersecurity investments ship enterprise worth. One of the vital invaluable belongings any healthcare supplier has is affected person belief. Extra healthcare suppliers want to contemplate the best way to create safe buyer experiences with zero belief.
TeleSign CEO Joe Burton advised VentureBeat that whereas buyer experiences range considerably relying on their digital transformation targets, it’s important to design cybersecurity and 0 belief into buyer workflows. That’s wonderful recommendation for healthcare suppliers underneath siege by attackers as we speak.
“Clients don’t thoughts friction in the event that they perceive that it’s there to maintain them protected,” Burton stated, including that machine studying is an efficient know-how for streamlining the consumer expertise whereas balancing friction. He advised VentureBeat that prospects may acquire reassurance from friction {that a} model, firm or healthcare supplier has a sophisticated understanding of cybersecurity and, most significantly, of the significance of defending affected person information and privateness.